Findings
A finding is a discovery of significance made following the completion of a scan. Findings result from the default out-of-the-box implementation of rule sets called Finding policies.
View all findings
To view different types of findings associated with all projects or packages in your tenant:
- From the left sidebar, navigate to Findings.
- The preset filters help you in locating the findings that matter most to you.
- Choose Prioritized Findings to view a list of critical vulnerability findings in the last 30 days that have either a reachable function or a reachable dependency, are not test dependencies, and have an available fix.
- Choose from a list of options under Code Dependencies to view a list of SCA, Vulnerability, Operational, License Risk, Malware or AI model findings.
- Choose Secrets to find a list of findings related to exposed secrets.
- Choose from a list of options under CI/CD to view findings related to GitHub Actions and CI/CD Tools.
- Choose RSPM to view findings related to repository’s security posture.
- Choose Containers to view container findings.
- Use Saved Filters to create and save your frequently used searches, helping you save time.
- Search for findings using basic filters.
- Toggle Advanced and search for findings using advanced filters.
- To apply exceptions to findings, select findings and click Actions > Add Exception.
- To export findings, select the findings, and click Actions > Export Selected or Export All.
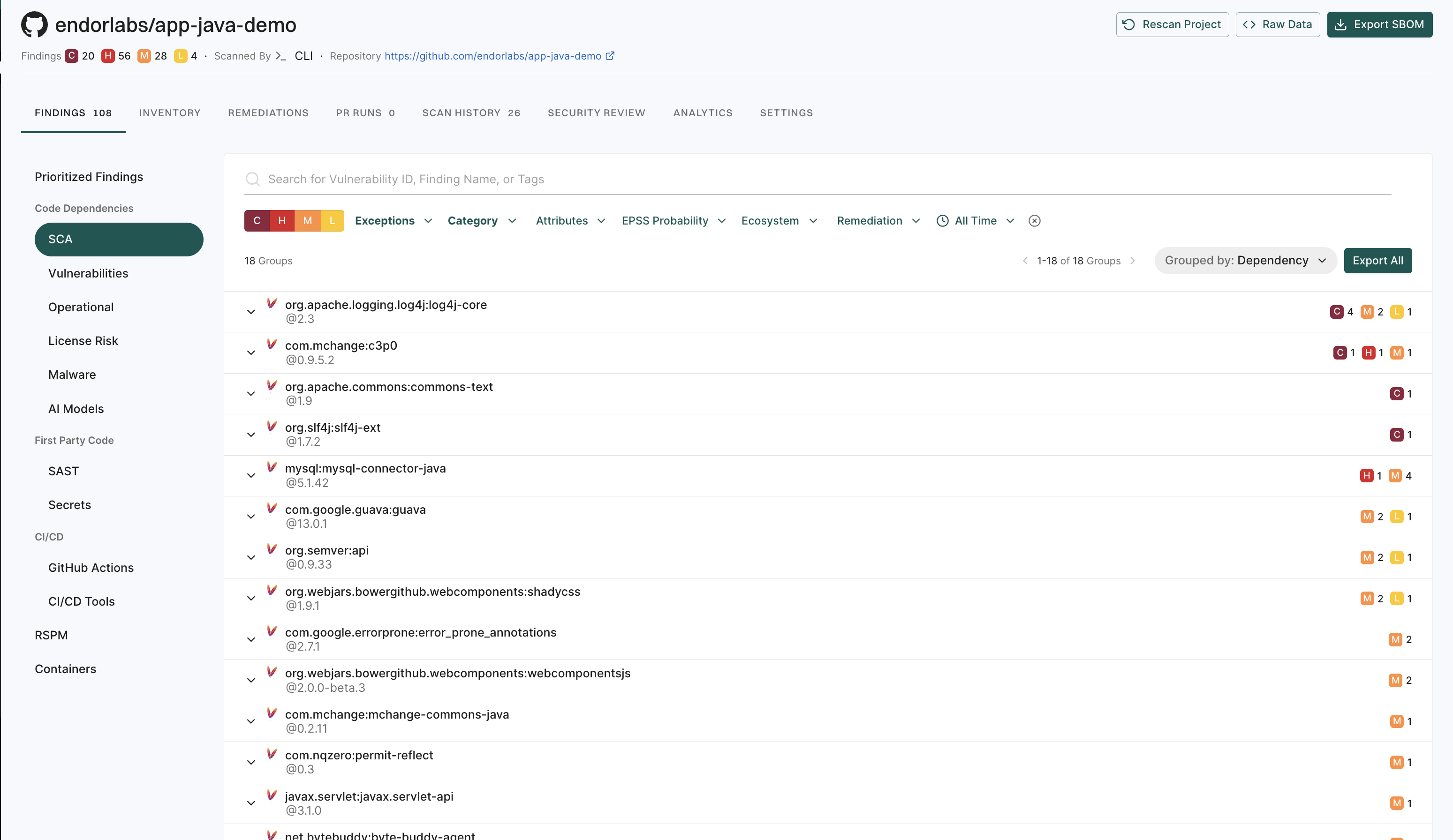
View findings associated with a project
To view the findings associated with a project:
- From the left sidebar, navigate to Projects.
- Select the project for which you want to view the findings. The Findings page includes the list of findings specific to the project.
- Review the list of findings. Click the finding to see its details.
Finding attributes
Finding attributes are characteristics or properties associated with each discovered issue or result obtained from a scan. These attributes could include the following details and metadata.
| Attribute | Description |
|---|---|
| Blocker | Finding was marked as blocking by an action policy. |
| Direct | Finding applies to a direct dependency. |
| Disputed | The CVE reported in this finding is has been marked as ‘disputed’. |
| Exception | Finding was marked as exempt from action policies by an exception policy. |
| Exploited | The CVE reported in this finding is actively exploited and is listed in the Known Exploited Vulnerabilities (KEV) database. |
| External Path Only | Finding applies to a transitive dependency that can only be reached via external, non-OSS, project paths. |
| First Party | Finding applies to a dependency that belongs to the same namespace. |
| Fix Available | A fix is available for the CVE reported in this finding. |
| Invalid Secret | Finding applies to an invalid secret. |
| Malware | Finding applies to a malicious package. |
| Normal | Finding applies to a normal, non-test, dependency. |
| Notification | Finding triggered a notification based on an action policy. |
| Phantom | Finding applies to a phantom dependency. |
| Policy Based | Finding was generated by a Rego based finding policy. |
| Potentially Reachable Dependency | Finding applies to a potentially reachable dependency. |
| Potentially Reachable Function | Finding applies to a potentially reachable function. |
| Reachable Dependency | Finding applies to a reachable dependency. |
| Reachable Function | Finding applies to a reachable function. |
| Same Repository | Finding applies to a dependency that belongs to the same project. |
| Self | Finding applies only to the analyzed package version, there is no dependency involved. |
| Test | Finding applies to a dependency that is not in production code. |
| Transitive | Finding applies to a transitive (indirect) dependency. |
| Under Review | Finding applies to suspicious package under review. |
| Unfixable | There is no fix available for the CVE reported in this finding. |
| Unreachable Dependency | Finding applies to an unreachable dependency. |
| Unreachable Function | Finding applies to an unreachable function. |
| Valid Secret | Finding applies to a valid secret. |
| Warning | Finding triggered a warning based on an action policy. |
| Withdrawn | The CVE reported in this finding is has been marked as ‘withdrawn’. |
View GitHub Action findings
GitHub Actions is a CI/CD platform that allows you to automate your build, test, and deployment pipelines. You can create workflows that build and test pull requests to your repository, or deploy merged pull requests to production. To mitigate vulnerabilities within the supply chain, comprehensive visibility into GitHub Action workflows and their relationships in your repository is crucial. You can then proceed to identify and fix weak points within the system.
When you run an endorctl scan, it detects GitHub Action workflows used in your repository. It proceeds to scan all the repositories included in the detected workflows and creates findings. The GitHub Action is mapped as a package and discovers direct and transitive dependencies.
To view GitHub Action findings:
- From the left sidebar, navigate to Projects.
- Search for and select a project and select Findings.
- Click GitHub Actions under CI/CD to view GitHub Actions findings.
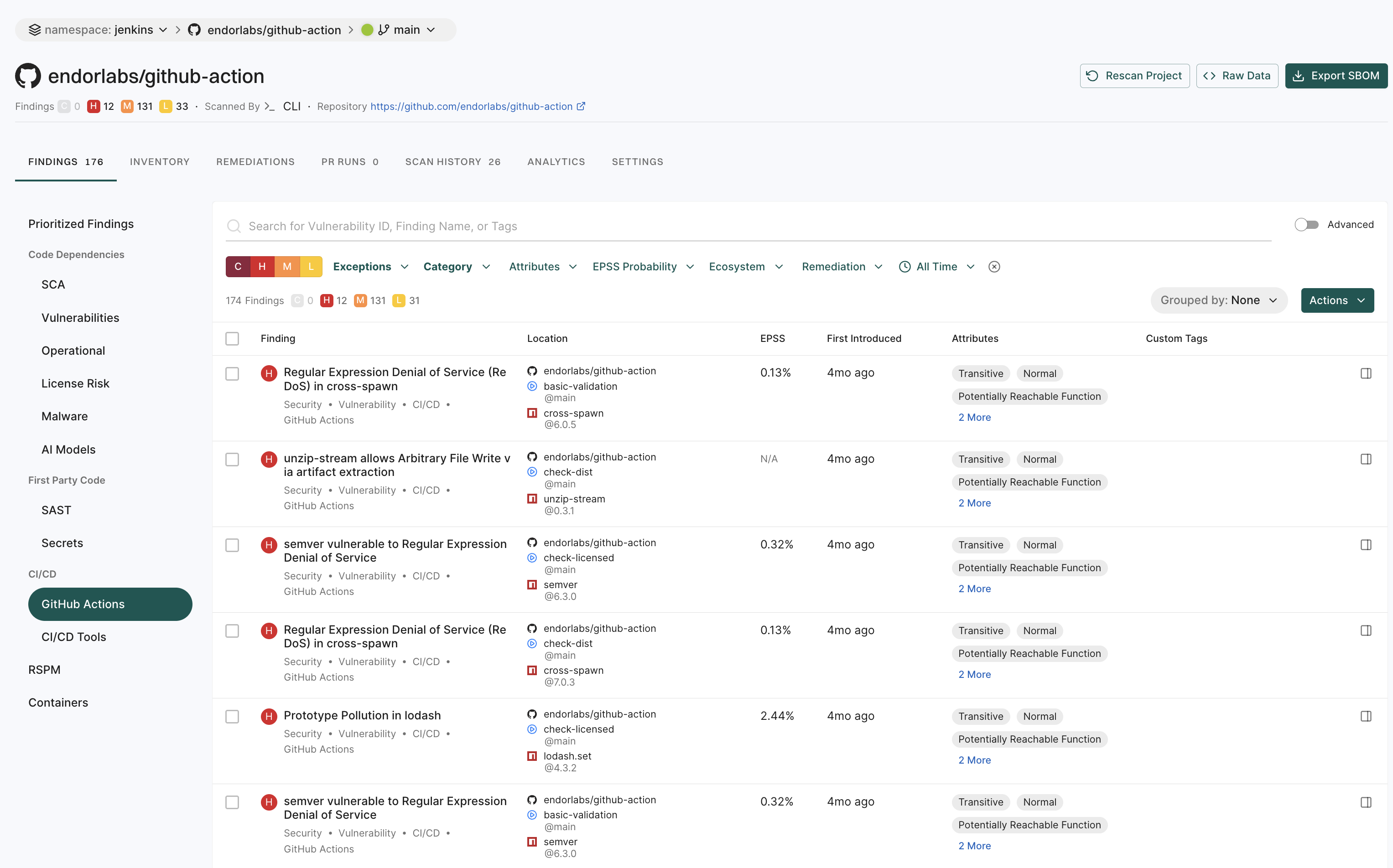
Note
- Vulnerabilities and dependencies associated with GitHub Action packages written in JavaScript or TypeScript are detected by Endor Labs.
- Private GitHub Actions and private reusable workflows referenced from other repositories are not detected.
- Test dependencies are not detected for GitHub Action packages.
Search for findings using basic filters
Use the following basic filters to search for information in your findings.
- C - Findings with critical severity.
- H - Findings with high severity.
- M - Findings with medium severity.
- L - Findings with low severity.
- Exceptions - Filters findings based on the exception policies. See Filter using Exception Policies to learn more about filtering findings using exception policies.
- Category - Choose from CI/CD, Malware, license risks, operational risks, RSPM, GitHub actions, SAST, AI models, containers, secrets, security, supply chain, or vulnerability and view related findings.
- Remediations - Narrow down vulnerabilities based on their fix status. Endor Patch Available filters findings where an Endor-provided patch is available to fix the vulnerability. Recommended Upgrade Available filters findings where a recommended version upgrade is available.
- Attributes - Narrow down the list based on a range of factors such as:
- if a patch is available to fix the findings
- if the vulnerable function is reachable
- if the dependency is reachable
- if the dependency originates from a current repository or a current tenant
- if the dependency is a test dependency
- if the dependency is a phantom dependency
- if the finding originates from itself, direct, or a transitive dependency
- filter the findings by the Exploited tag from CISA KEV
- filter the findings by the Warn or Break the Build options set in the action policy
- EPSS Probability - Choose the Exploit Prediction Scoring System (EPSS) score range.
- All Time - Choose a time range.
- Eco System - Choose from available options to filter based on a language or an ecosystem.
Filter findings using Exceptions
Use the following options to filter findings using exceptions.
- Hide Exceptions - Toggle it to view/hide exceptions from the findings display.
- Choose from one of the existing exception policies in the list or search for a specific exception using Search Policy Name.
- Select from the following reasons why you are applying this exception:
- In Triage: The finding has been triaged for more information.
- False Positive: The finding is a false positive.
- Risk Accepted: The risk associated with the finding is accepted.
- Other: Another reason applies for this exception.
- Expires Within - Filter exceptions by expiration time-frame.
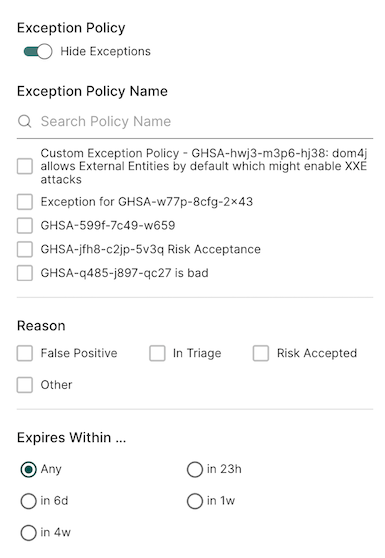
See Create exception policy for details on how to create and apply exceptions.
Search for findings using advanced filters
Use advanced filters to create powerful queries that drill deeper into the dataset to fetch results with a specific context.
Search using the advanced filters applies to all the branches of a repository. You can retrieve results from any branch by specifying the relevant context ID or type.
For example:
-
If the default branch for the
BenchmarkJavarepository is set tomaster, applying filters with the context ID formastershows results specific to branch.To scan from the default branch, run the following command :
endorctl scan --path=. -
Similarly, if there is another branch named
test-branch, switching to that branch shows results specific to the branch.To scan the branch, run the following command:
git checkout test-branch endorctl scan --path=.
After running the sans, you can view the findings specific to the branches in the Endor Labs user interface.
-
Select Projects from the left sidebar.
-
Select the project for which you want to view the findings.
-
At the top left of the page, you’ll find a drop-down menu that allows you to select the specific branch. The default branch of the repository is selected by default.
In the following example,
masteris the default branch. To view findings from other branches (for example,test-branch), choose the desired branch from the drop-down menu.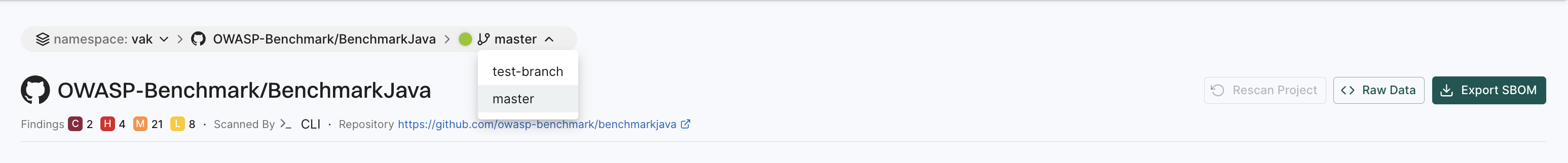
Tip
Check Projects to see the default branch of your project. To change the default branch, use--as-default-branch while performing the endorctl scan. See scanning strategies for information on testing and monitoring different versions of your code.
The Advanced Filters use the GetFinding API call to fetch results.
The following table lists some example attributes, you can use in your custom API calls. See also example combinations below.
| Attribute | API Query |
|---|---|
| Severity | spec.level in ["FINDING_LEVEL_CRITICAL","FINDING_LEVEL_HIGH"] |
| Category | spec.finding_categories contains ["FINDING_CATEGORY_VULNERABILITY"] |
| Fixable | spec.finding_tags contains ["FINDING_TAGS_FIX_AVAILABLE"] |
| Reachability | spec.finding_tags contains ["FINDING_TAGS_REACHABLE_FUNCTION"] |
| Ecosystem | spec.ecosystem in ["ECOSYSTEM_MAVEN"] |
| EPSS score greater than 10% | spec.finding_metadata.vulnerability.spec.epss_score.probability_score > 0.1 |
| EPSS score less than or equal to 100 | spec.finding_metadata.vulnerability.spec.epss_score.probability_score <= 1 |
| Only query a given project | spec.project_uuid=="UUID of the project" |
Examples
Show all findings of critical vulnerability and high severity that have a fix available, with a reachable function and EPSS score greater than 10%.
spec.level in ["FINDING_LEVEL_CRITICAL","FINDING_LEVEL_HIGH"] and spec.finding_tags contains ["FINDING_TAGS_FIX_AVAILABLE"] and spec.finding_tags contains ["FINDING_TAGS_REACHABLE_FUNCTION"] and spec.finding_metadata.vulnerability.spec.epss_score.probability_score > 0.1
Show vulnerabilities for a specific project.
spec.finding_categories contains ["FINDING_CATEGORY_VULNERABILITY"] and spec.project_uuid == "660e2bc48c7d4e60a5fc692f"
Show vulnerabilities for a specific language in a specific project.
spec.finding_categories contains ["FINDING_CATEGORY_VULNERABILITY"] and spec.ecosystem in ["ECOSYSTEM_PYPI"] and spec.project_uuid == "660e2bc48c7d4e60a5fc692f"
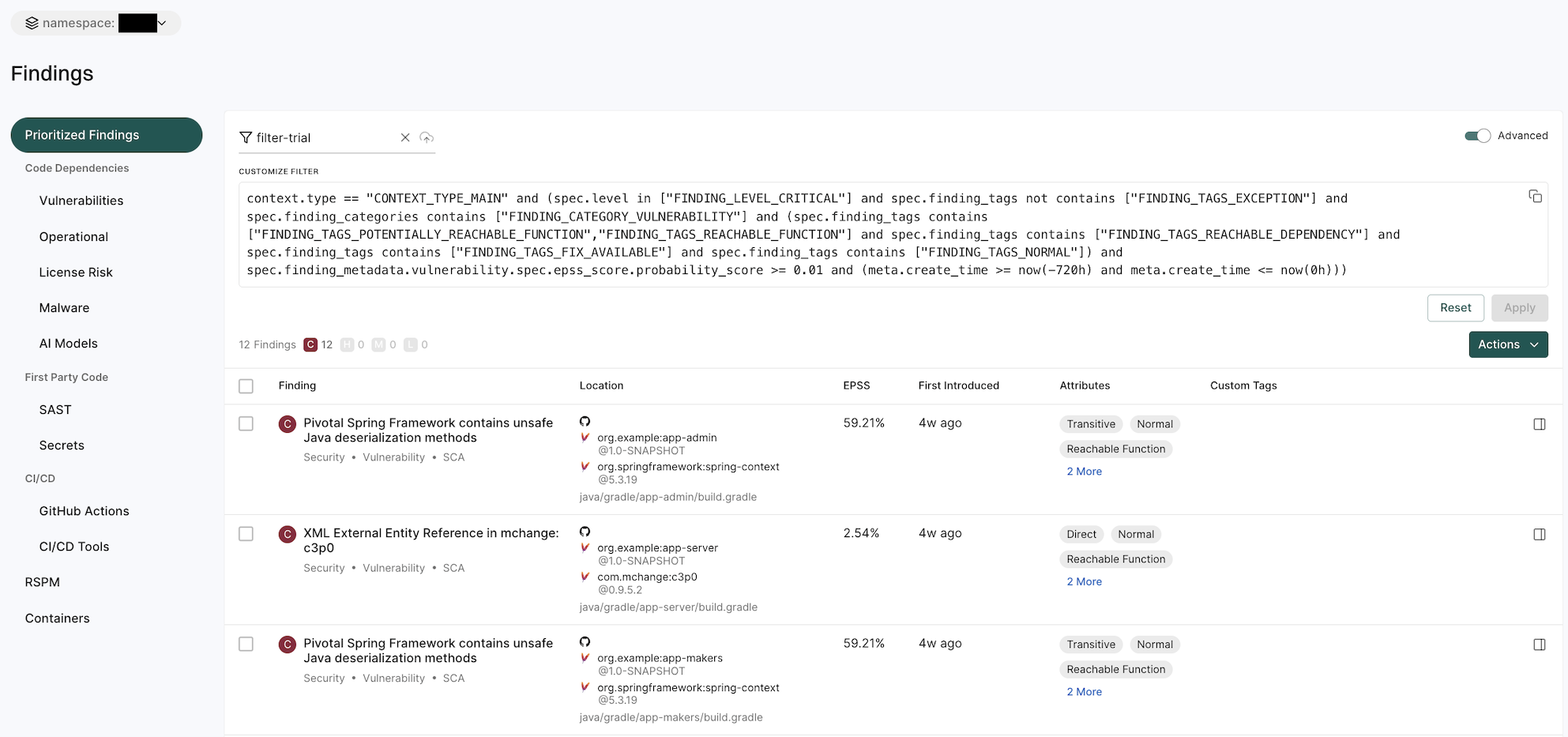
Saved filters
Saved filters are customizable filter settings that users can create and reuse across projects in Endor Labs. They improve efficiency by eliminating the need to manually recreate filters. You can save the advanced search filters that you created to fetch curated search results. Saved queries are visible in the drop-down list.
To create a saved filter:
- Select Findings from the left sidebar.
- Toggle Advanced in the top right corner.
- Type the query in CUSTOMIZE FILTER.
- Enter a title in the field with the filter icon.
- Click Save New Filter.
Manage saved filters
To delete a saved filter:
- Navigate to Manage > Settings from the left sidebar.
- Select SAVED FILTERS.
- Click the vertical three dots on the right side of the filter you want to delete and click Delete.
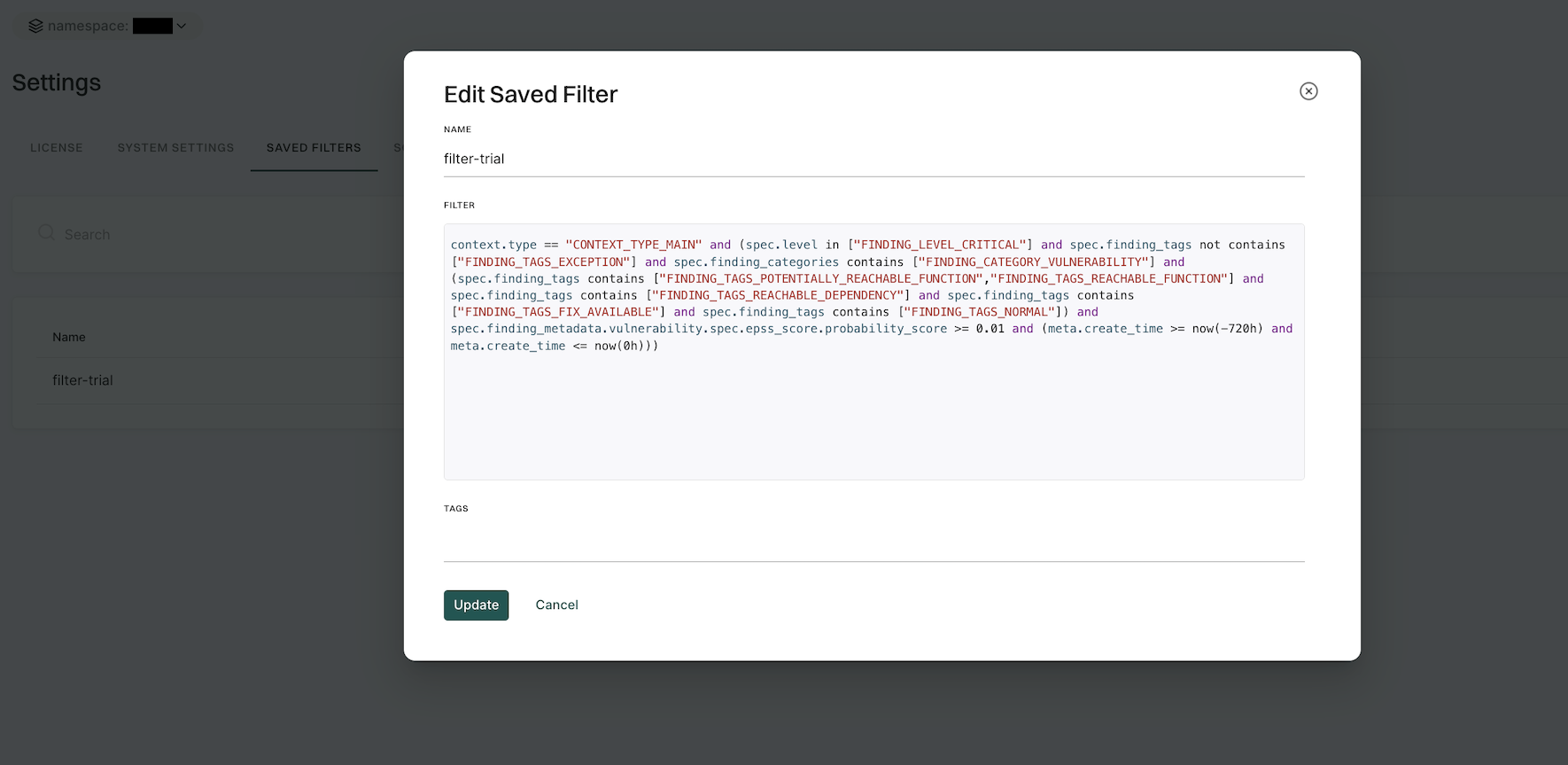
To edit a saved filter:
- Navigate to Manage > Settings from the left sidebar.
- Select SAVED FILTERS.
- Click the vertical three dots on the right side of the filter you want to edit and click Edit
- You can update the name, query, and tags.
- Click Update to save the updated changes.
Search for exceptions
Findings that are associated with exception policies do not trigger notifications.
To search for findings that are associated with exceptions,
- From the left sidebar, navigate to Projects.
- Search for and select a project, and select Findings.
- From the DEPENDENCY tab, choose Basic Filters.
- Click Exceptions and toggle Show Exceptions.
- You can search for a specific exception policy name, reason, or expiry range to filter the relevant results.
Manage findings
See Finding policies for details on how to configure findings.
Act on findings
See Action policies for details on how to define and trigger workflows based on findings that meet a given set of criteria.
Export findings
Users can export finding details to a CSV file for offline analysis.
- From the left sidebar, navigate to Projects.
- Search for and select a project and select Findings.
- Search for findings using advanced or basic filters.
- Click Export Findings and select the fields that you want to include in the CSV file.
- Click Export to CSV. The file is downloaded to your system.
Apply exception to findings
Add an exception policy to prevent this finding from triggering action policies in future scans.
- From the left sidebar, navigate to Projects.
- Search for and select a project, and select Findings.
- Search for findings using advanced or basic filters.
- Click a finding and from Actions choose Add Exception. See Create exception policy for details on how to create and apply exceptions.
Apply tags to findings
Tagging findings helps you organize, prioritize, and filter issues efficiently. You can tag findings in a finding policy or while running the endorctl scan.
Using finding policies
You can define custom tags in a finding policy, which automatically apply to findings that match its conditions. See Finding policies for more information.
To add custom tags:
- Sign in to Endor Labs and select Policies & Rules from the left sidebar.
- Follow the steps to create a finding policy. Ensure to add your choice of custom tags in Finding Custom Tags. You can also update an existing policy.
- Click Create Finding Policy.
After you create or update a finding policy, rescan your project to apply the custom tags to your findings.
Through the CLI
When scanning projects using endorctl, you can tag all the findings generated within the scan scope using the --finding-tags flag.
To scan and tag all findings of a endorctl scan:
endorctl scan --finding-tags=findings-tag-name
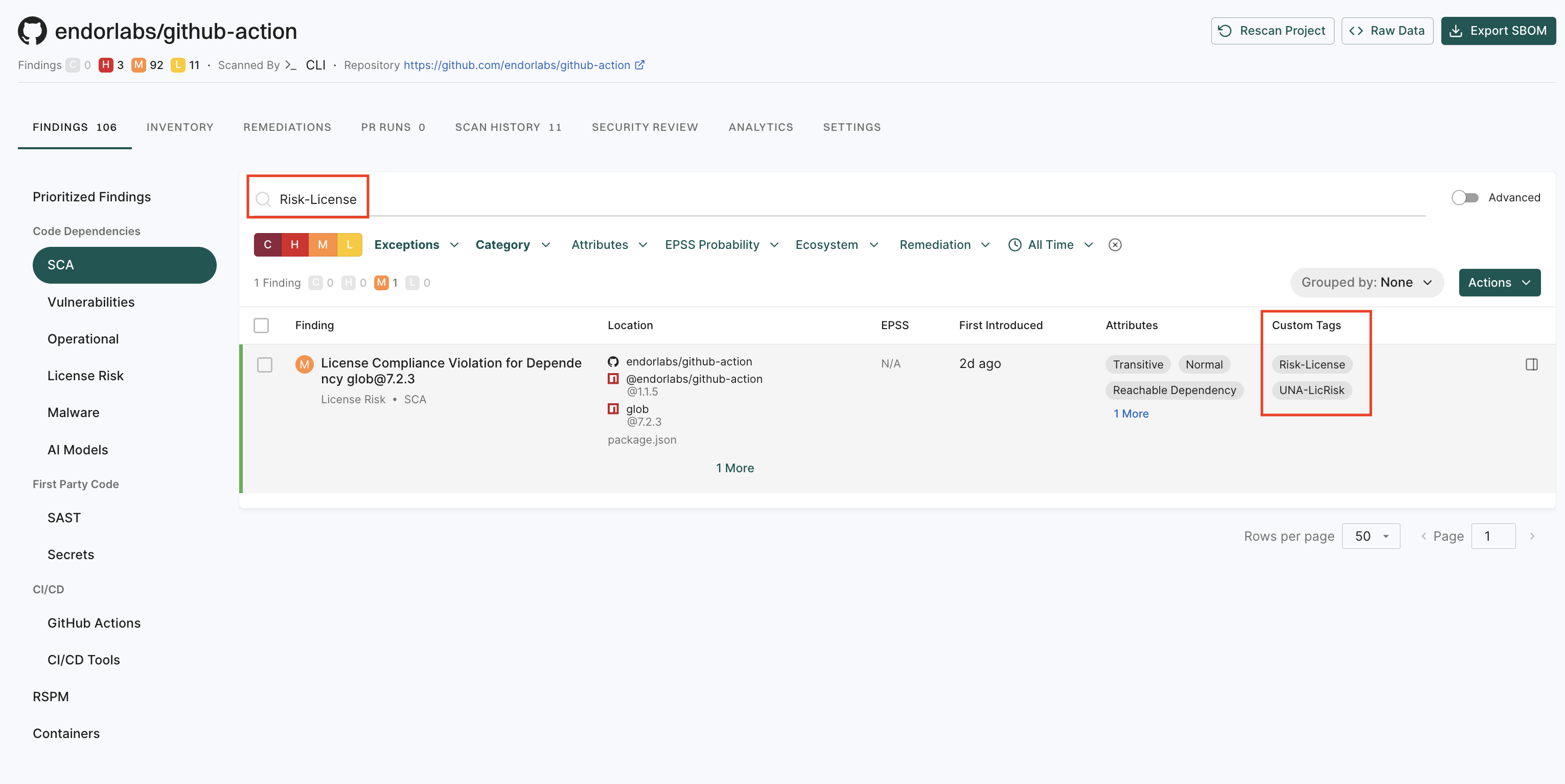
View tagged findings
To filter and view the findings by their tags:
-
Sign in to Endor Labs and select Projects > Findings.
-
Enter the tag in the search bar to filter and view findings by tag name.
View Remediations
If you enable upgrade impact analysis, you can view the remediation recommendation when you select a finding, if available.
Click View Details to view the details of the remediation recommendation.
Click View Full Recommendation to view all available upgrade paths.
Feedback
Was this page helpful?
Thanks for the feedback. Write to us at support@endor.ai to tell us more.
Thanks for the feedback. Write to us at support@endor.ai to tell us more.