Scan artifacts and binaries (Beta)
You can now perform endorctl scan on your binaries and artifacts with out requiring access to source code or build systems. Scan Java and Python packages that are pre-built, bundled, or downloaded into your local system by specifying a file path to your artifact or binary package.
Endor Labs scans the specified package, producing vital scan artifacts such as details about resolved dependencies and transitive dependencies, along with comprehensive call graphs. It enables you to acquire valuable insights and improve the security and reliability of the software components.
To successfully scan your applications:
Check software pre-requisites
- You can scan artifacts from Java and Python projects.
- You can scan JAR, WAR, and EAR package file formats built using Maven with a pom.xml configuration file.
- You can scan EGG(tar.gz) and Wheel(.whl) package file formats.
- If you have a private registry and internal dependencies on other projects, you must configure private registries for the Python and Java projects. See Configure package manager integrations.
- When performing deep scans make sure that you have the following minimum system specification requirements:
- 4-core processor with 16 GB RAM for small projects
- 8-core processor with 32 GB RAM for mid-size projects
- 16-core processor with 64 GB RAM for large projects
Understand the scan arguments
Use --package as an argument to scan artifacts or binaries. You must provide the path of your file using --path and specify a name for your project using --project-name.
endorctl scan --package --path --project-name
Run the scan
Use the following options to scan your repositories.
Option 1 - Quick scan
Perform a quick scan of the local packages to get quick visibility into your software composition. This scan won’t perform reachability analysis to help you prioritize vulnerabilities.
Syntax:
endorctl scan --quick-scan --package --path=<<specify-the-path-of-your-file>> --project-name=<<specify-a-name-for-the-project>>
Example:
endorctl scan --quick-scan --package --path=/Users/username/packages/logback-classic-1.4.10.jar --project-name=package-scan-for-java
Option 2 - Deep scan
Use the deep scan to perform dependency resolution, reachability analysis, and generate call graphs. You can do this after you complete the quick scan successfully.
Syntax:
endorctl scan --package --path=<<specify-the-path-of-your-file>> --project-name=<<specify-a-name-for-the-project>>
Example:
endorctl scan --package --path=/Users/username/packages/logback-classic-1.4.10.jar --project-name=java-package-scan
View results
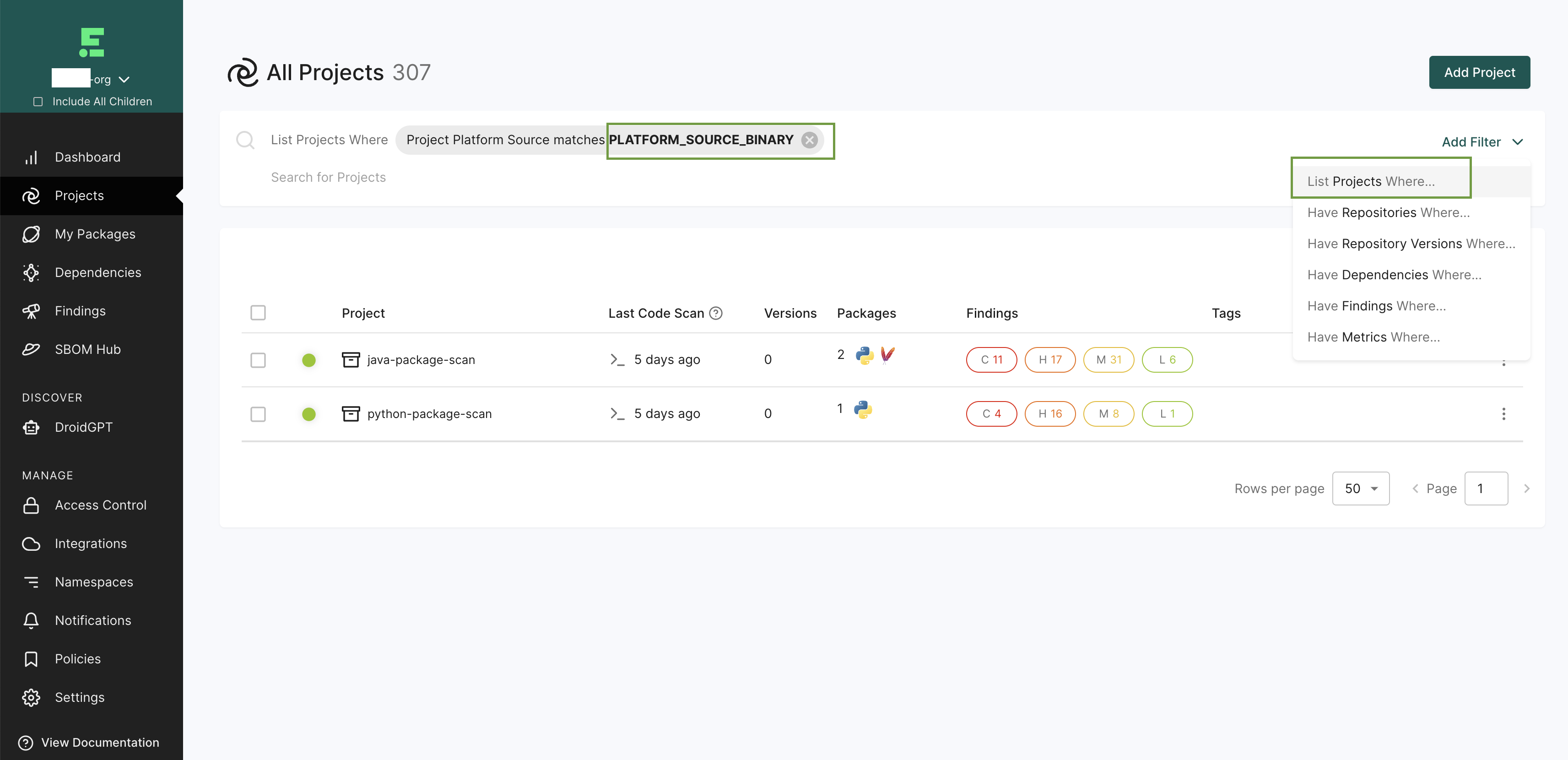
You can sign into the Endor Labs user interface, click the Projects on the left sidebar, and find your project using the name you entered to review its results.
You can view the list of projects created for scanning packages using the parameter Project Platform Source matches PLATFORM_SOURCE_BINARY to search on Projects.
Feedback
Was this page helpful?
Thanks for the feedback. Write to us at support@endor.ai to tell us more.
Thanks for the feedback. Write to us at support@endor.ai to tell us more.