Endor Labs Vulnerability Database
A vulnerability is a security weakness in a software package that attackers can exploit to compromise systems, steal data, or disrupt operations. Open-source software often contains vulnerabilities that can introduce risks to your organization, if not managed properly.
Endor Labs vulnerability database is a comprehensive compilation of known software vulnerabilities. You can search the vulnerability database to identify and discover vulnerabilities within your software dependencies.
The following are the vulnerability IDs that can be used to search within the Endor Labs platform:
| Identifier type | Example | Description |
|---|---|---|
| CVE ID | CVE-2023-45678 | The most common global identifier for vulnerabilities. It is managed by MITRE and is widely used. |
| GHSA ID | GHSA-xxxx-xxxx-xxxx | GitHub Security Advisory ID for vulnerabilities reported by GitHub. |
| PySEC ID | PYSEC-2023-123 | Identifier for vulnerabilities in Python packages, sourced from the Python Packaging Advisory Database. |
| MAL ID | MAL-xxxx-xxxx | Identifier for malware advisories. The data is sourced from OSV and flags packages linked to malicious activity. |
meta.name or spec.aliases fields.
Search for a vulnerability
Search for vulnerabilities using supported security identifiers across your software dependencies.
-
Sign in to Endor Labs and select Discover > Vulnerabilities from the left sidebar.
-
Type a search query using a vulnerability ID (for example, CVE, GHSA) and click Search Vulnerabilities.

You can view detailed information including the name of the vulnerability, CVE ID, vulnerability’s severity, description, and metadata to help users quickly identify important details about a vulnerability.
-
Select Affected Packages to view a list of all software packages impacted by the identified vulnerability, including their names, introduced and fixed versions, and the source of the vulnerability data.
-
Select a package to view its details.
-
Overview: Shows affected and fixed versions, severity, available patches, impacted classes, and a link to the fix commit. It helps users understand the issue and take necessary remediation steps.
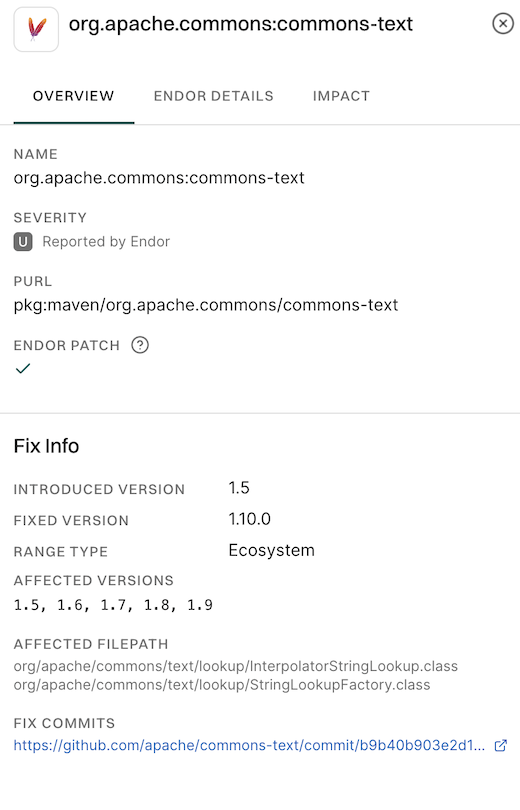
-
Endor Details: Shows affected call paths and file paths to help identify where the vulnerable code is used and how it may be triggered in the project
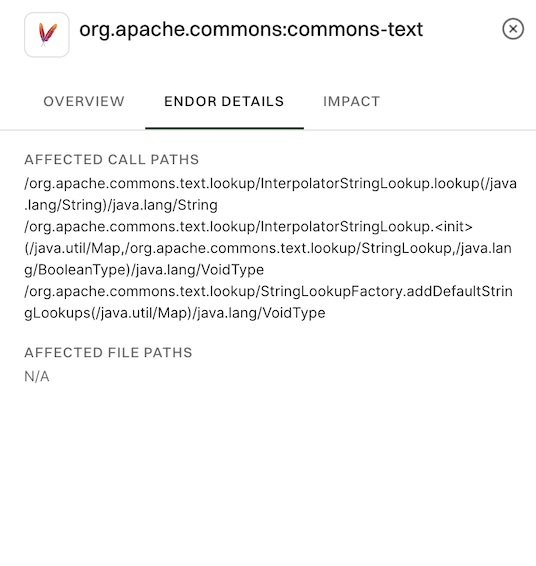
-
Impact: Shows each package version, along with the number of findings, how many projects use it, and how many other packages depend on it
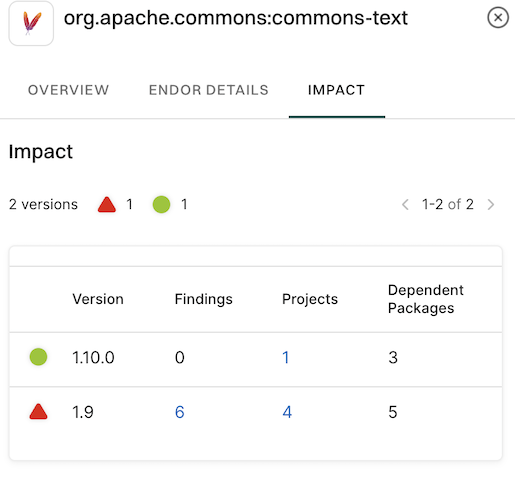
-
-
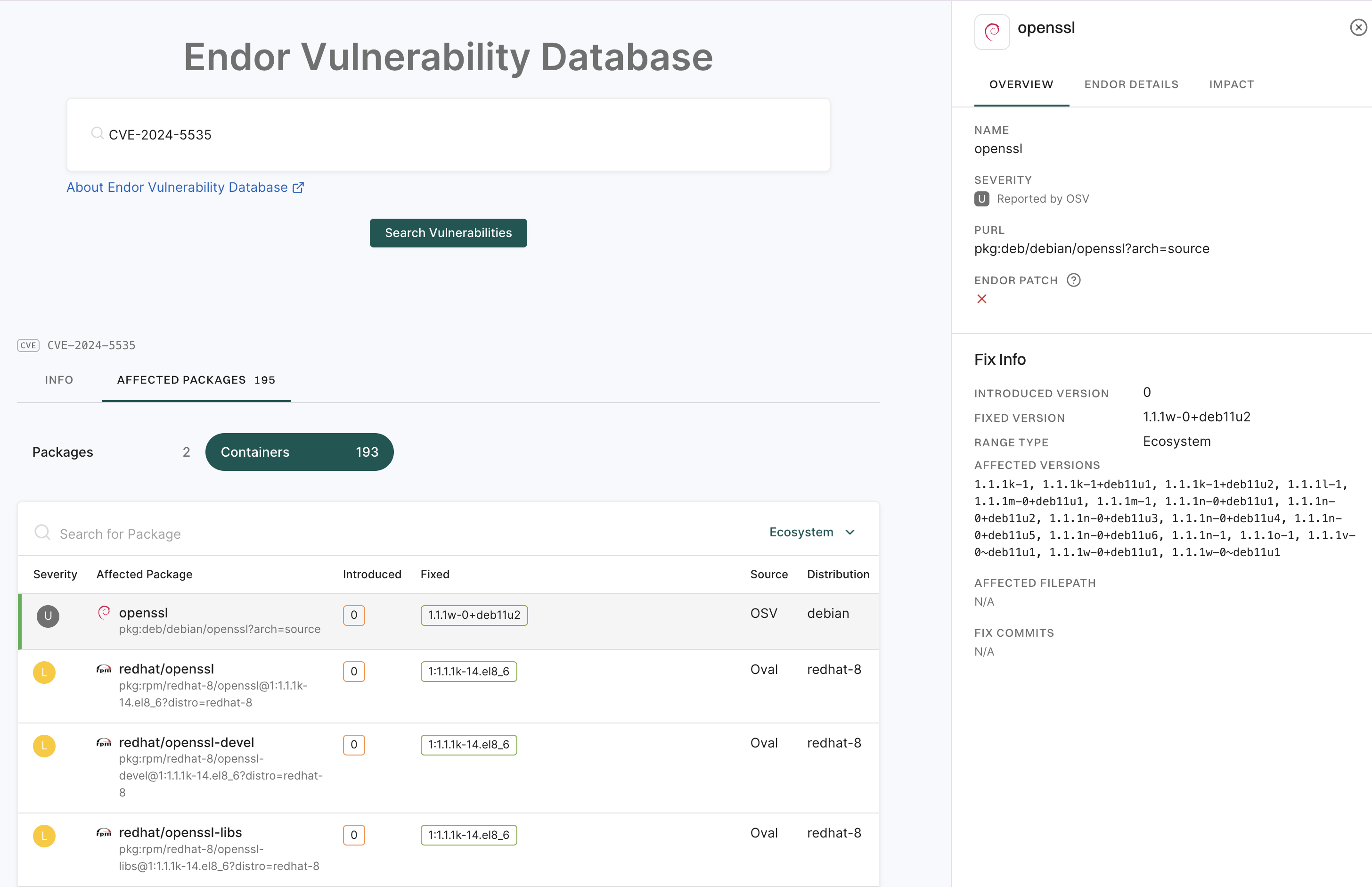
Select Containers to see all container images in your organization with known vulnerabilities. It lists which packages are affected, where the issues were introduced, whether fixes are available, and the severity of the issues.
Feedback
Was this page helpful?
Thanks for the feedback. Write to us at support@endor.ai to tell us more.
Thanks for the feedback. Write to us at support@endor.ai to tell us more.