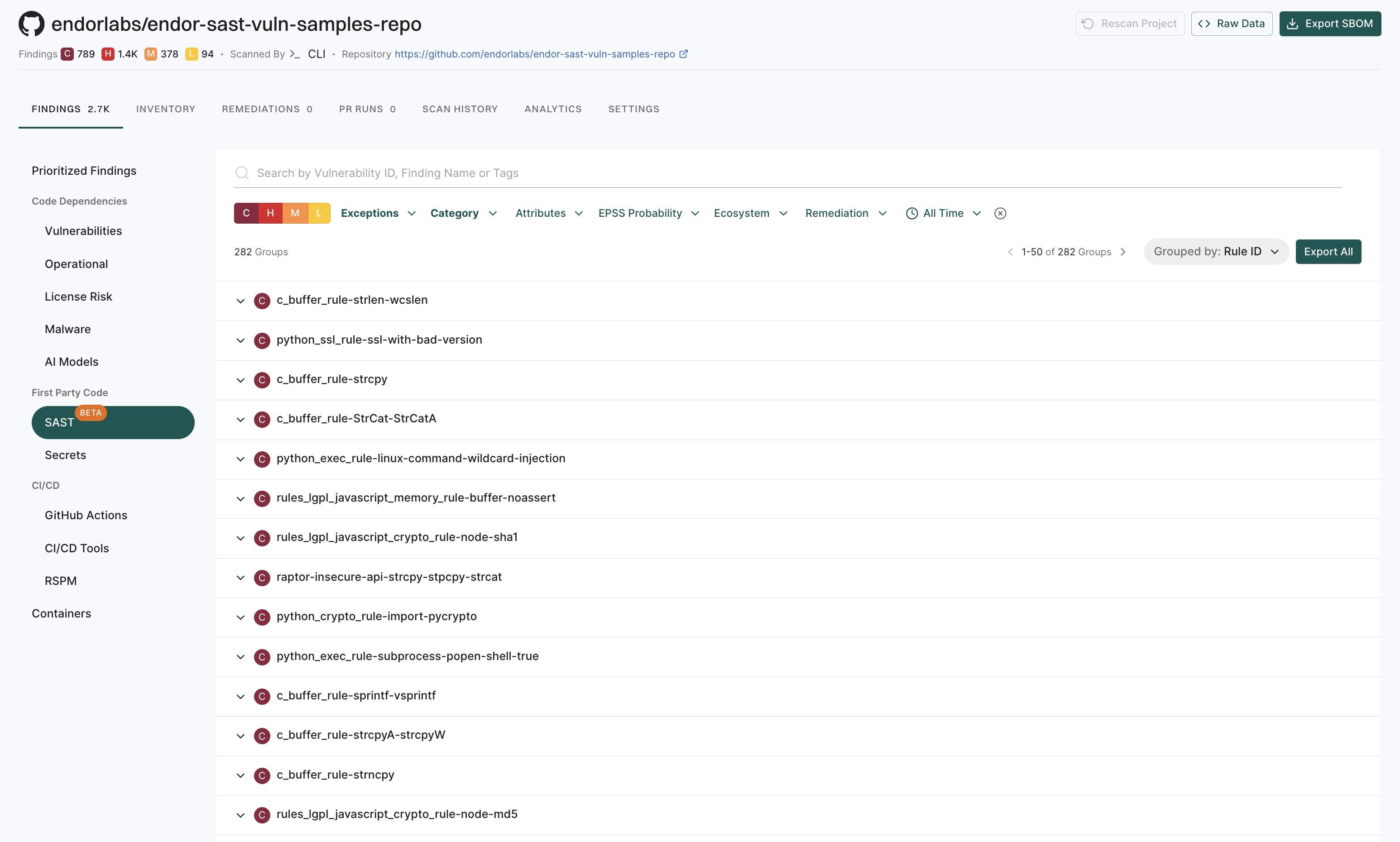
You can view SAST findings in the Findings page.
-
Select Findings from the left sidebar.
-
Select SAST under First Party Code.
-
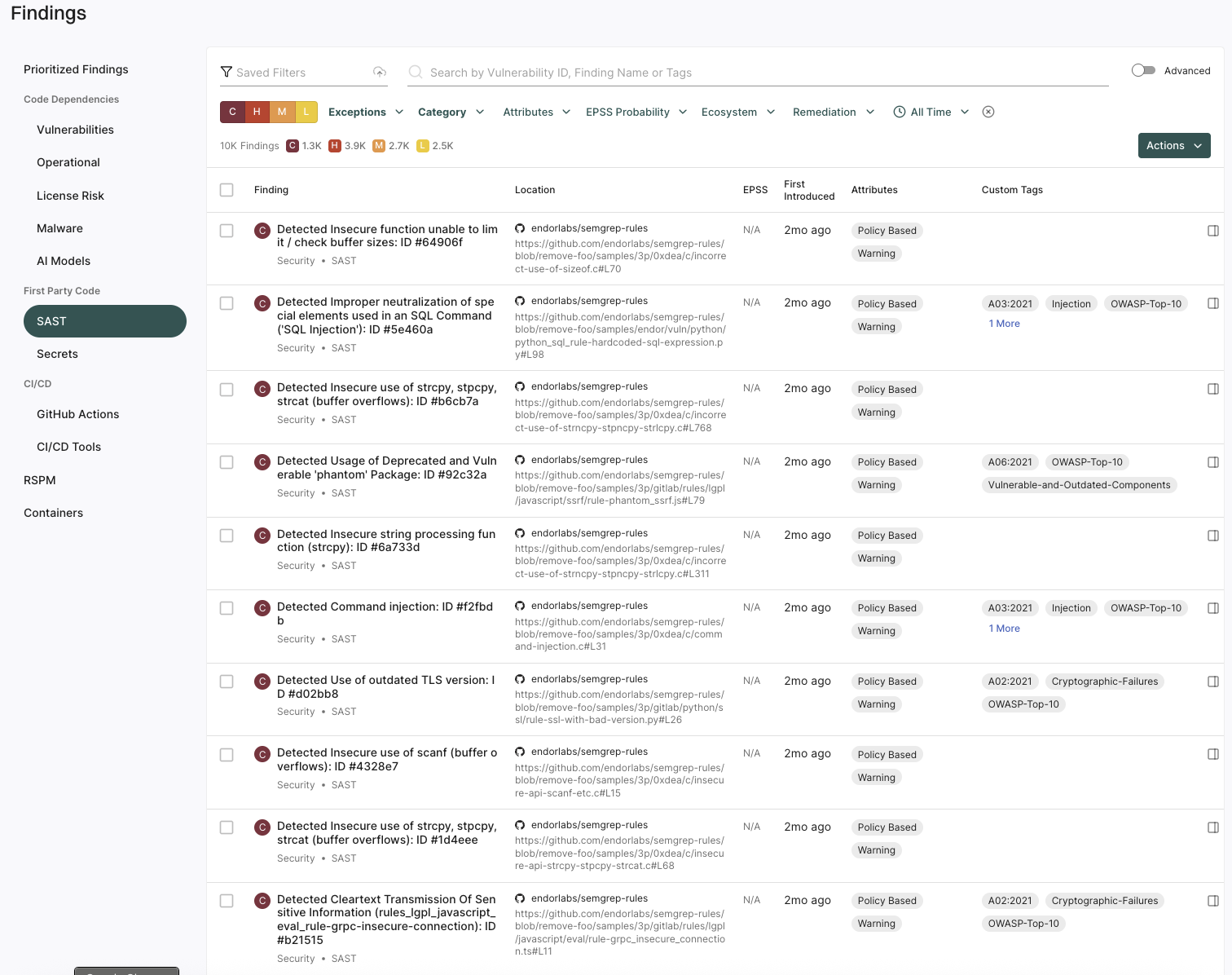
You can use the filters to further refine the SAST findings.
-
Select a row to view finding details.
-
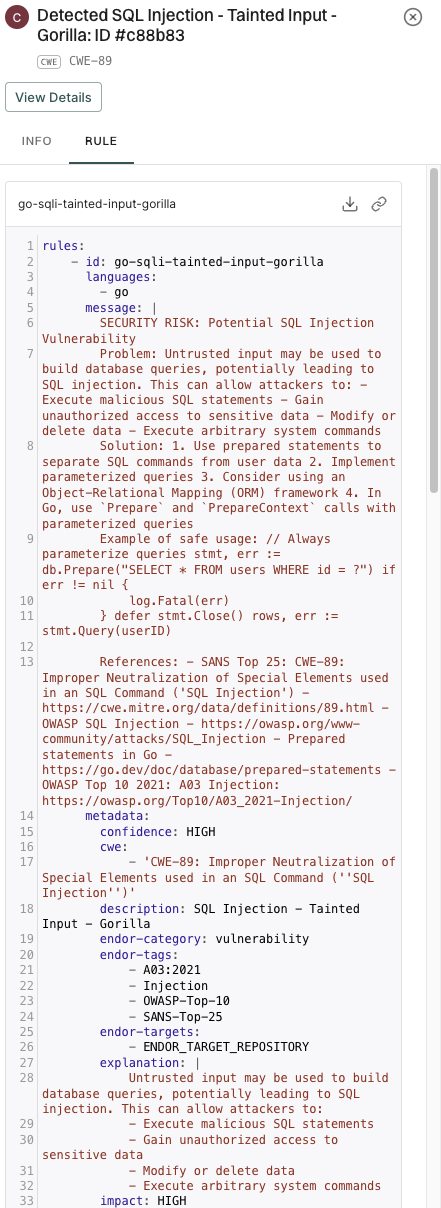
Select Rule to view the rule that triggered the finding.
-
To export findings as a CSV file, select the findings, click the vertical three dots, and select Export Selected or Export All. See export findings to learn more.
AI-analyzed SAST findings
When you run a SAST scan with --ai-sast-analysis=agent-fallback, an AI agent analyzes the findings to determine if they are true security issues or false positives. The AI agent automatically tags verified true positives with True Positive and false positives with False Positive for easy filtering.
To view AI-analyzed SAST findings:
- Select Findings from the left sidebar.
- Select SAST under First Party Code.
- Use the Attributes filter and select True Positive or False Positive to filter out whatever you want.
- Select a finding to view the details.
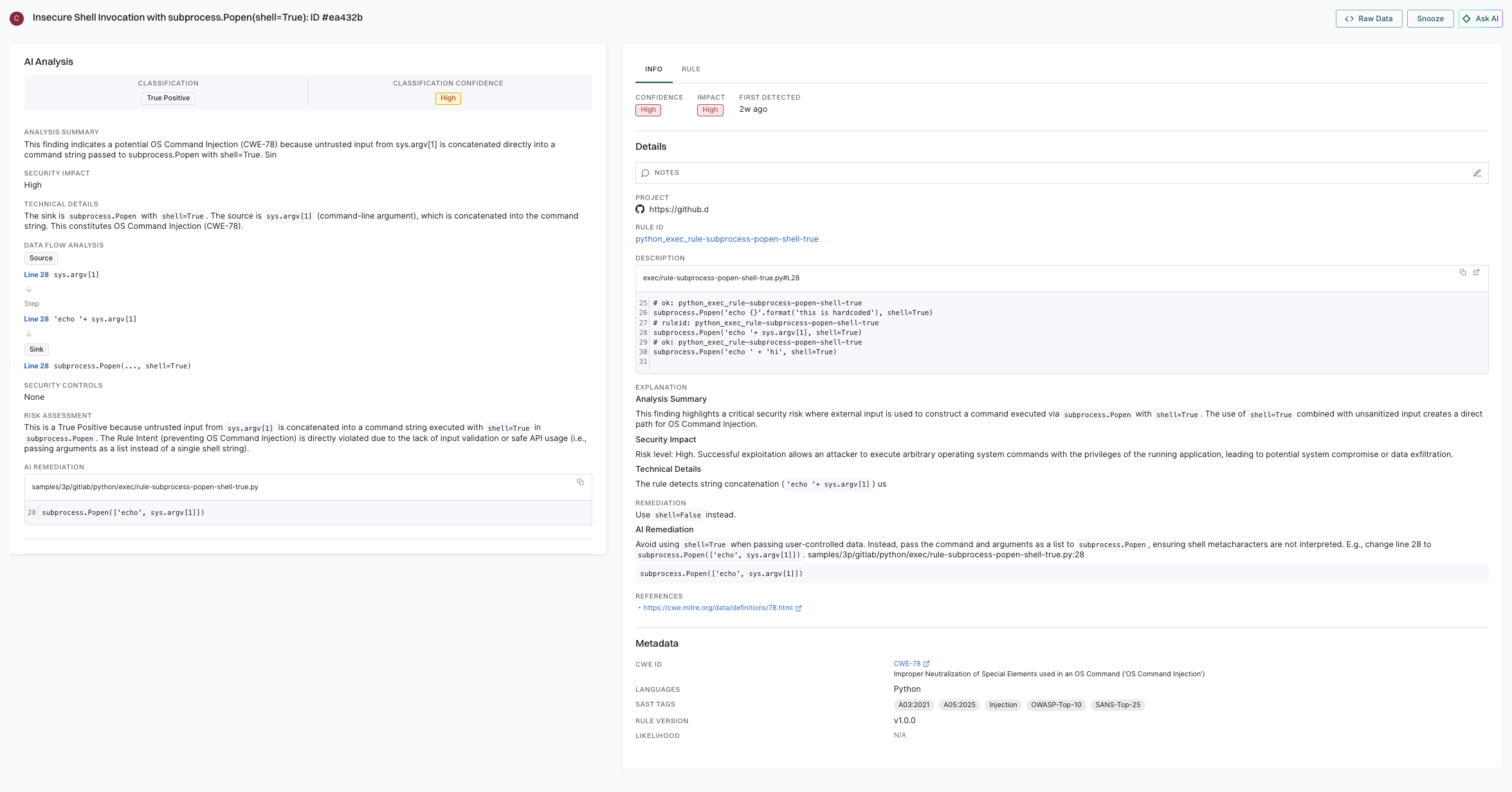
- AI Analysis: Indicates the AI agent’s classification and analysis of the finding.
- Classification: Specifies if the finding is categorized as a true positive or false positive, including the associated confidence level.
- Analysis Summary: A brief explanation of the security issue identified, including why the finding was triggered and what type of vulnerability it represents.
- Security Impact: The risk level and potential consequences if the vulnerability is exploited.
- Technical Details: Technical explanation of how the vulnerability can be exploited, including the source and sink points in the code.
- Data Flow Analysis: Traces how untrusted data flows through your code from input to the vulnerable point.
- Security Controls: Displays what security protections exist or are missing in the code.
- Risk Assessment: Detailed reasoning for why the finding is classified as a true positive or false positive, with supporting evidence.
- AI Remediation: Suggested code fix to address the vulnerability.
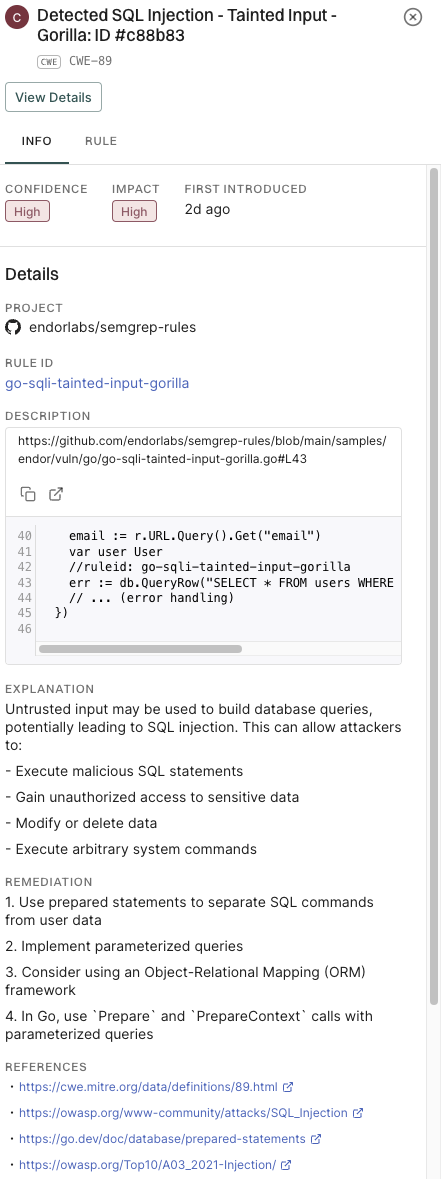
- Info, Rule, Explanation, and Metadata: Displays the underlying SAST rule information, detailed explanations of the security issue, remediation guidance, and metadata such as CWE classifications and security tags.
- Info: Contains key metadata for the finding, including confidence, impact, first detected time, project, and rule ID.
- Rule: The specific SAST rule that detected the finding, including rule description and code examples.
- Explanation: Analysis summary, security impact, and technical details about why this is a SAST finding.
- Remediation: General remediation guidance for addressing this type of vulnerability.
- References: Links to relevant security references such as CWE definitions.
- Metadata: Contains classification details such as the CWE ID, affected languages, security tags applied to the finding, and detected rule version.
- AI Analysis: Indicates the AI agent’s classification and analysis of the finding.
Group by filters for SAST findings
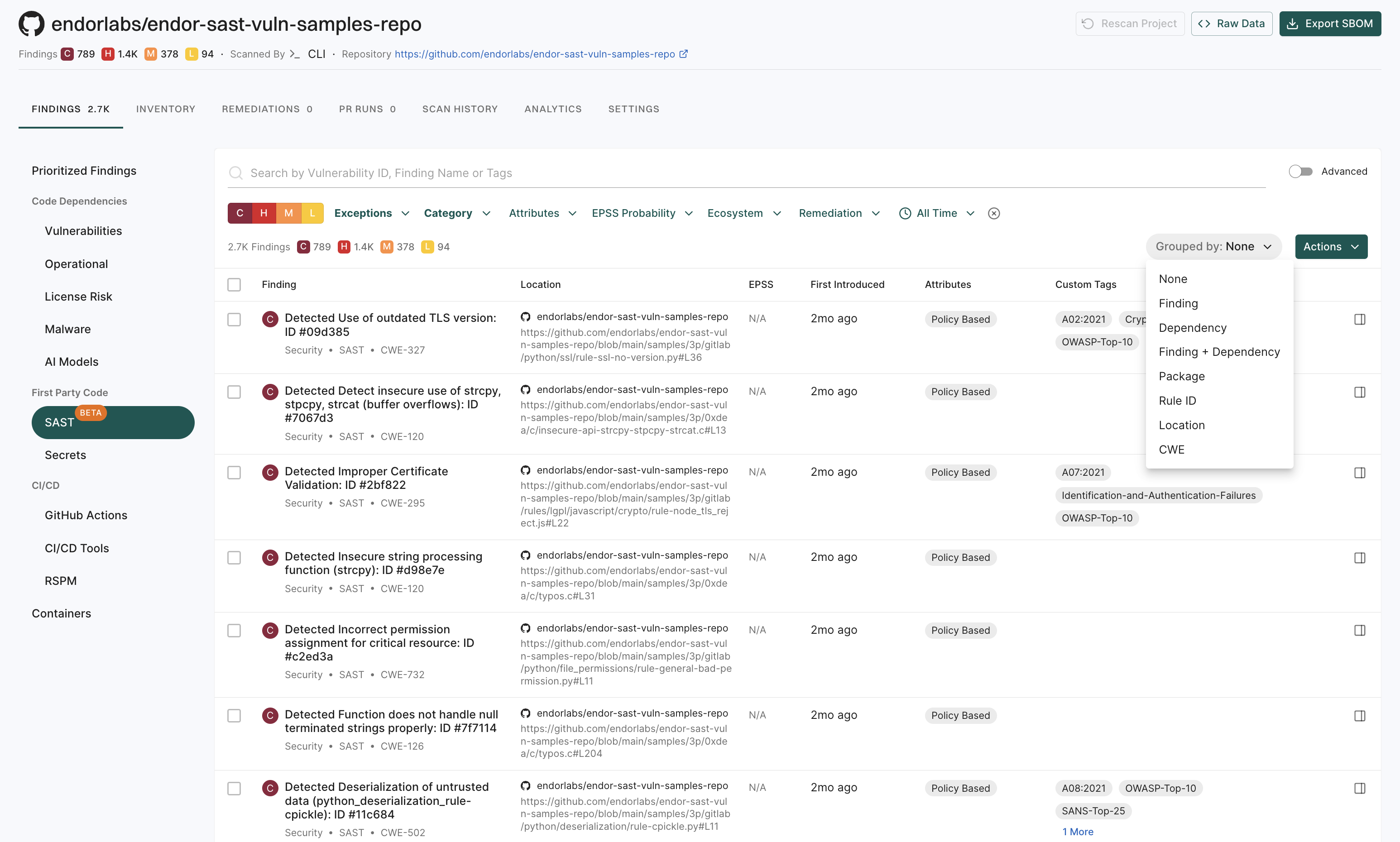
Use the group by filters to organize to have granular view of SAST findings in your project.
You can group findings by the following parameters for SAST:
- Findings
- Rule ID
- Location
-
From the left sidebar, select Projects.
-
Select the project for which you want to view the findings.
-
In the Findings page, select SAST under First Party Code.
-
Select the required group by filter, for example,
Rule ID.