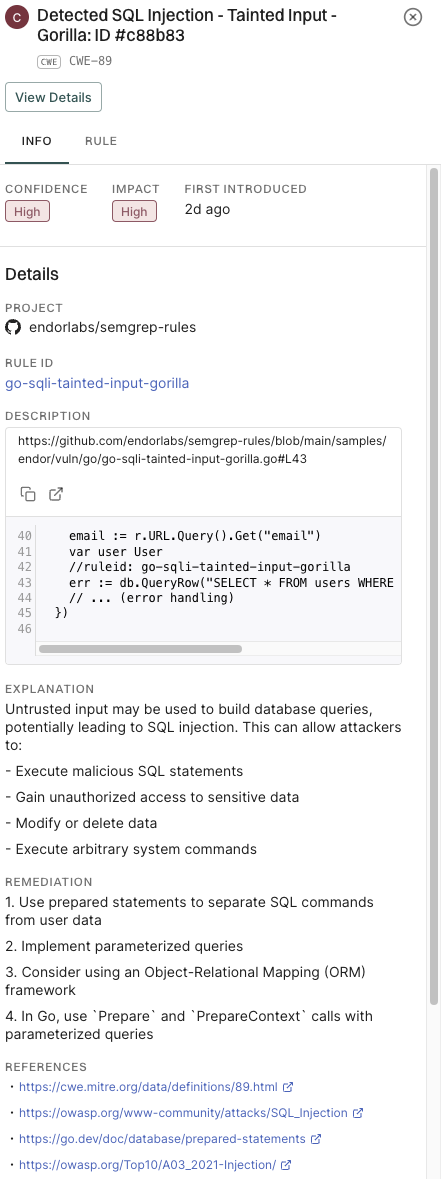
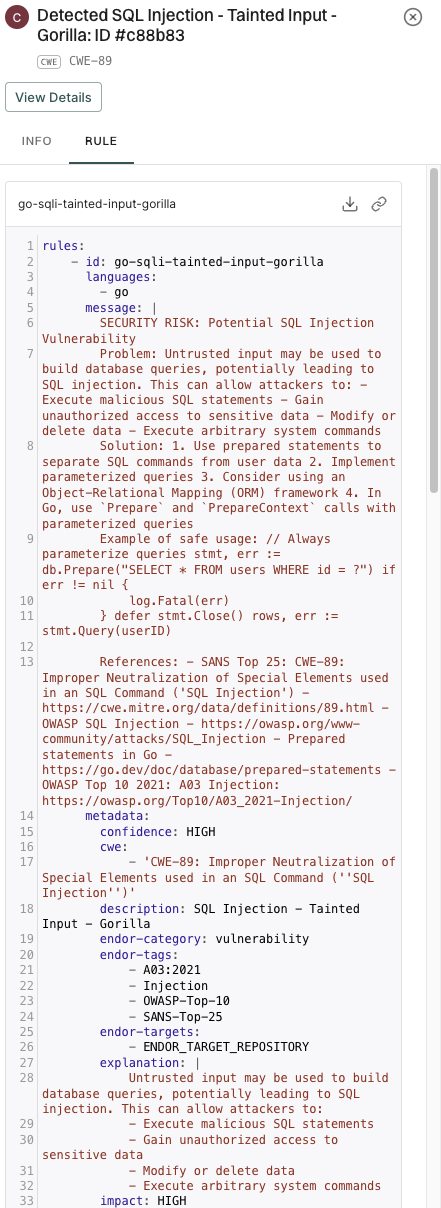
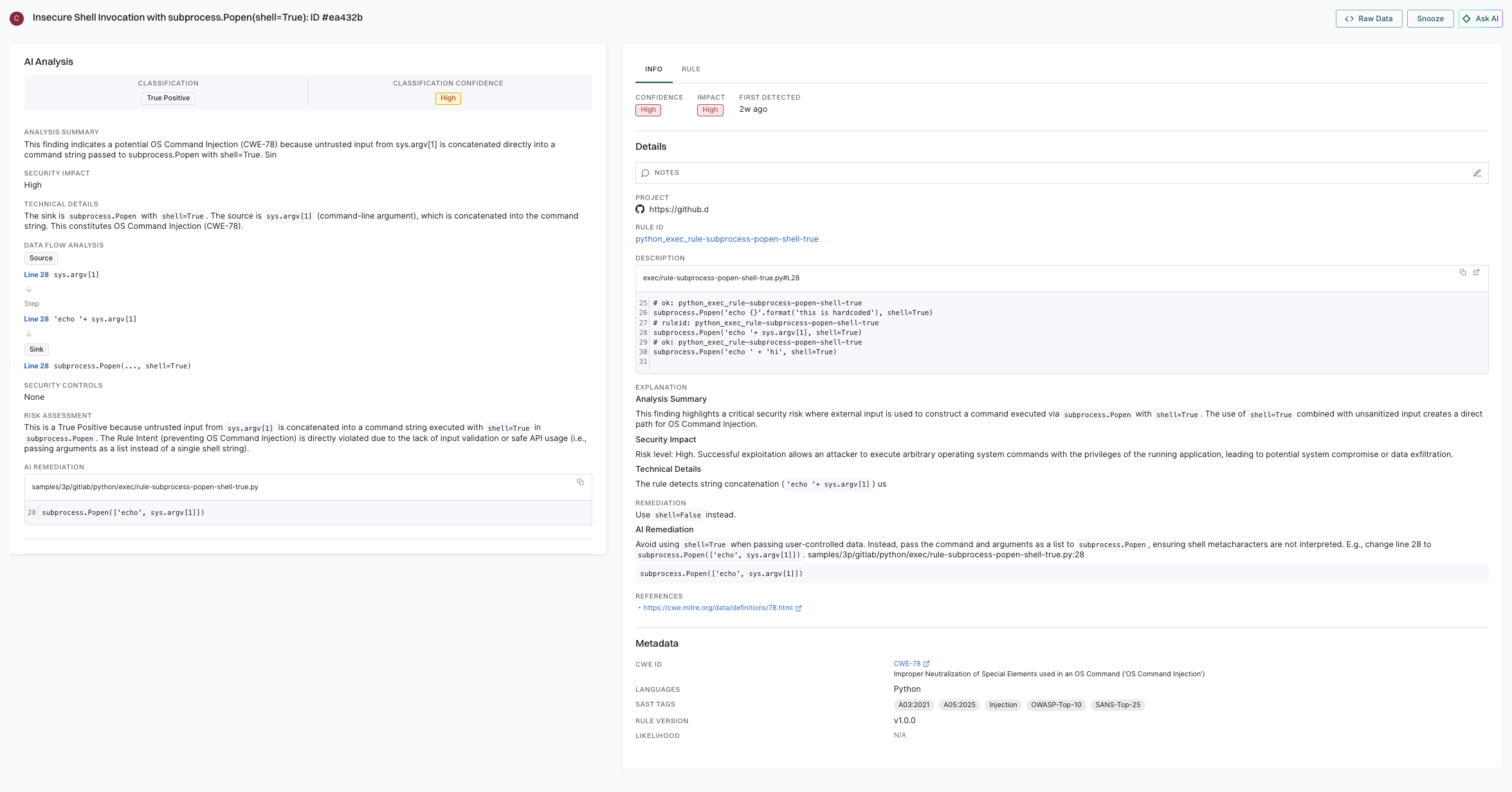
Static Application Security Testing (SAST) is an automated security analysis methodology that examines application code to identify potential security vulnerabilities.
SAST has the following characteristics:
- White-box Testing: Provides full visibility into application internals
- Non-runtime Analysis: Performs scans without code execution
- Early Detection: Identifies vulnerabilities during development phases
- Language Support: Analyzes multiple programming languages and frameworks
Endor Labs integrates Opengrep to provide SAST scan with endorctl.
Endor Labs enhances SAST scanning with AI analysis that evaluates each finding to determine whether it represents a genuine security vulnerability or a false positive. This automated classification streamlines your security workflow by eliminating the need for manual triage of every alert, allowing your team to prioritize and address real threats more efficiently. See AI analysis with SAST scan for more information.
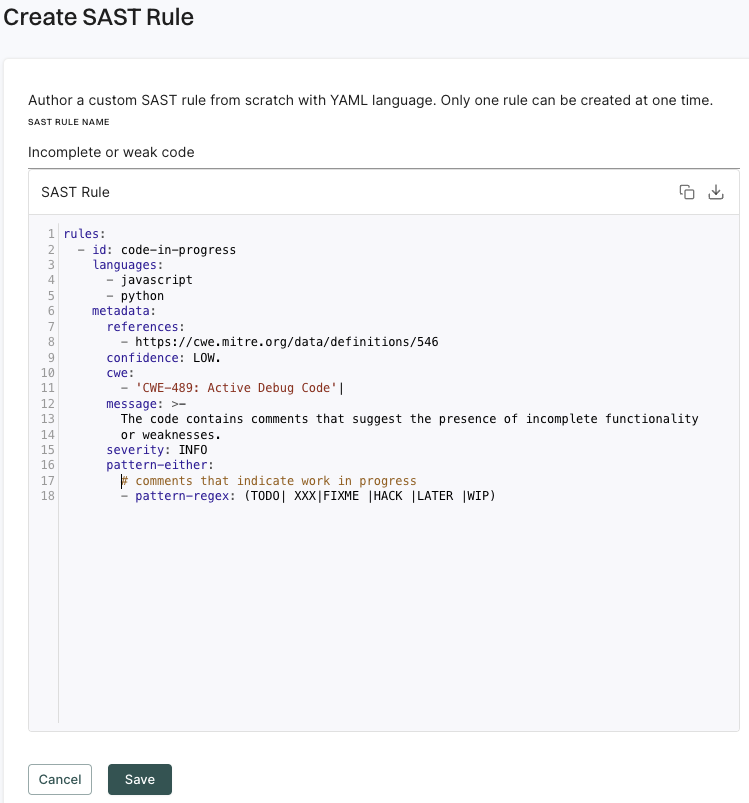
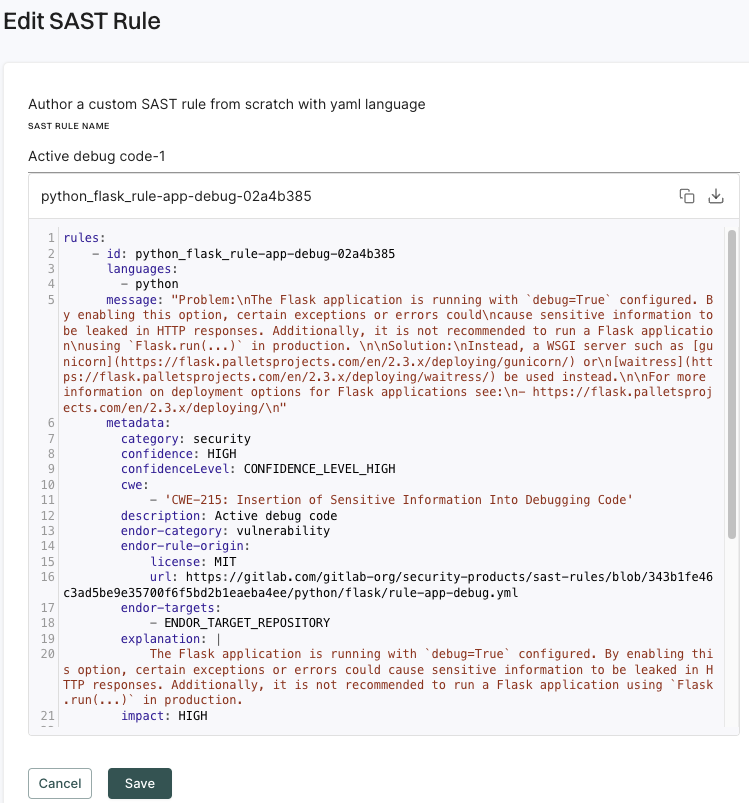
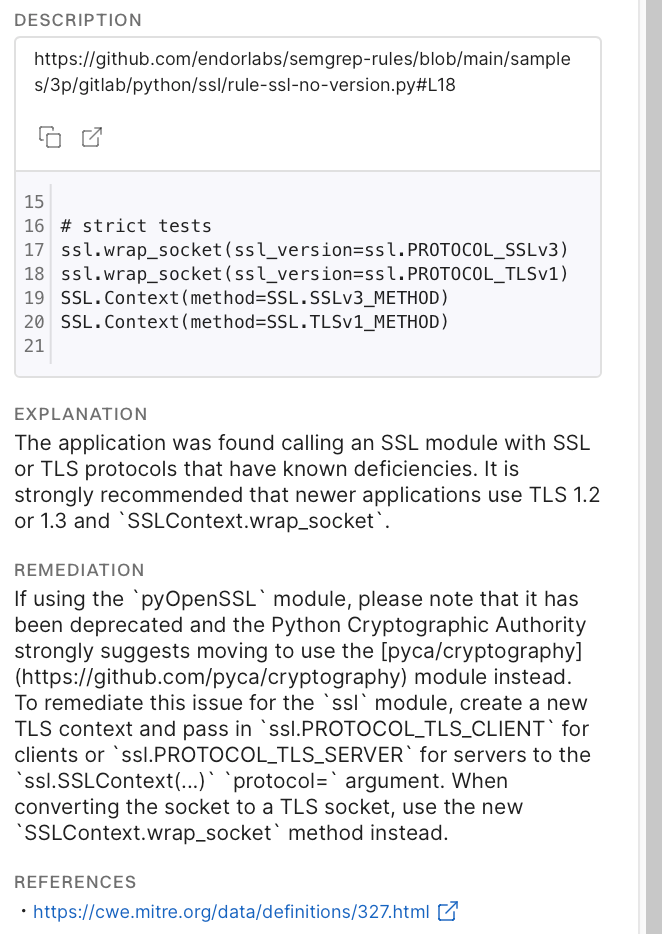
Opengrep is an open-source, static analysis tool that finds bugs and vulnerabilities in the source code using pattern matching. Opengrep parses the source code, applies pattern matching based on rules, and reports matches based on the rule specifications. Opengrep rules are in the yaml format.
When you run a SAST scan, Endor Labs downloads Opengrep and works seamlessly.
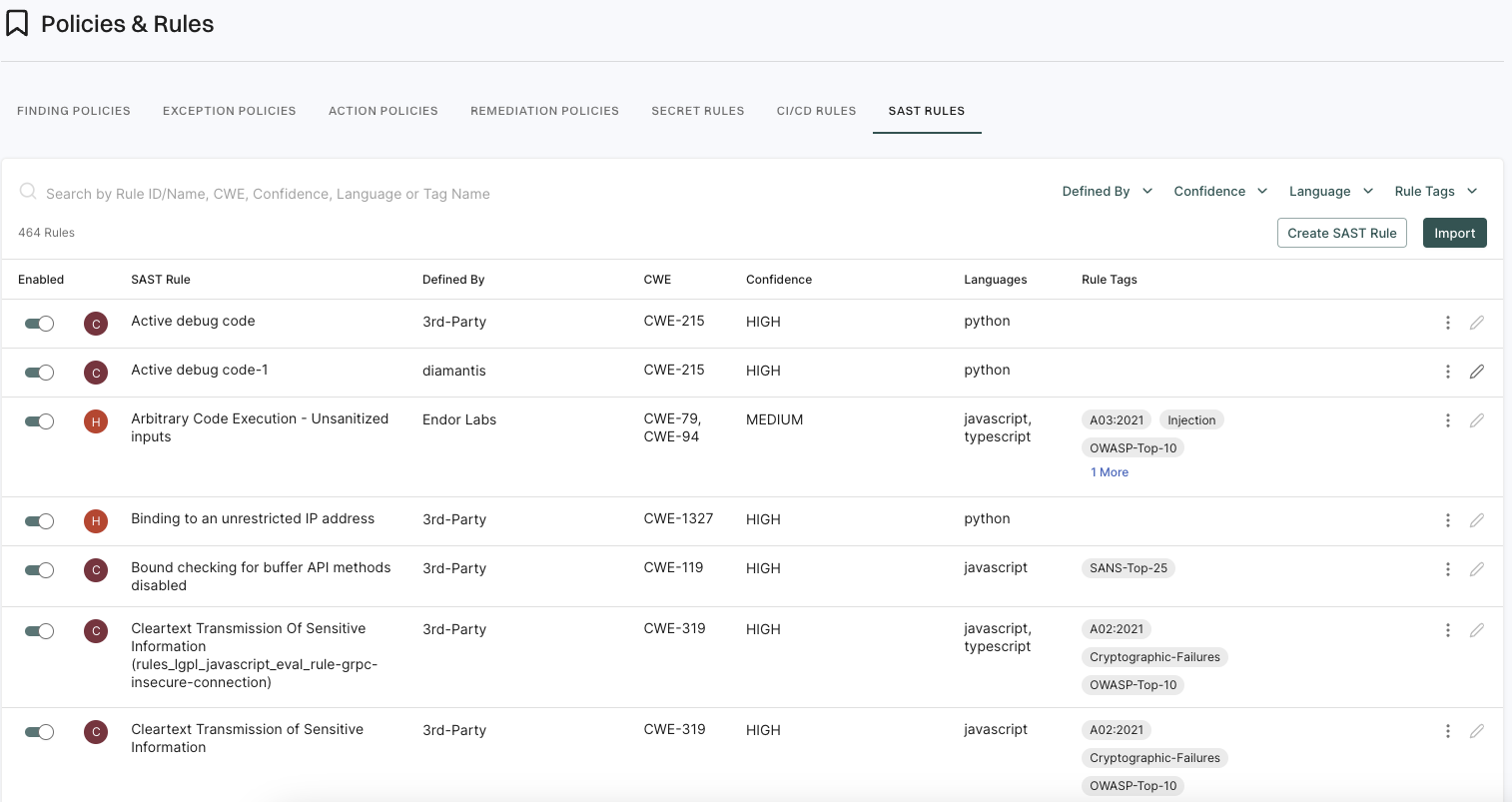
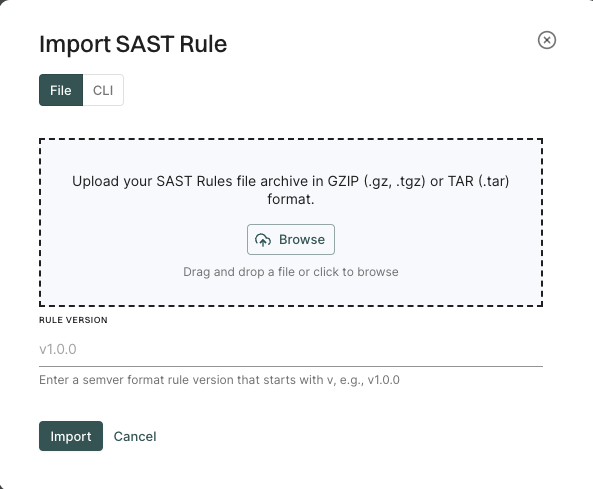
Endor Labs includes a set of curated rules. You can create your own rules or import rules with the rule designer.
When you scan with the SAST option enabled, Endor Labs uses Opengrep to scan for weaknesses in your source code based on the enabled rules and generates results based on the configured finding policies.
Tip
Endor Labs does not scan the files included in the
.gitignore files during SAST scan. You can also use the
nosemgrep annotation in the code to skip SAST scan. Refer to the
Semgrep Documentation for more information.
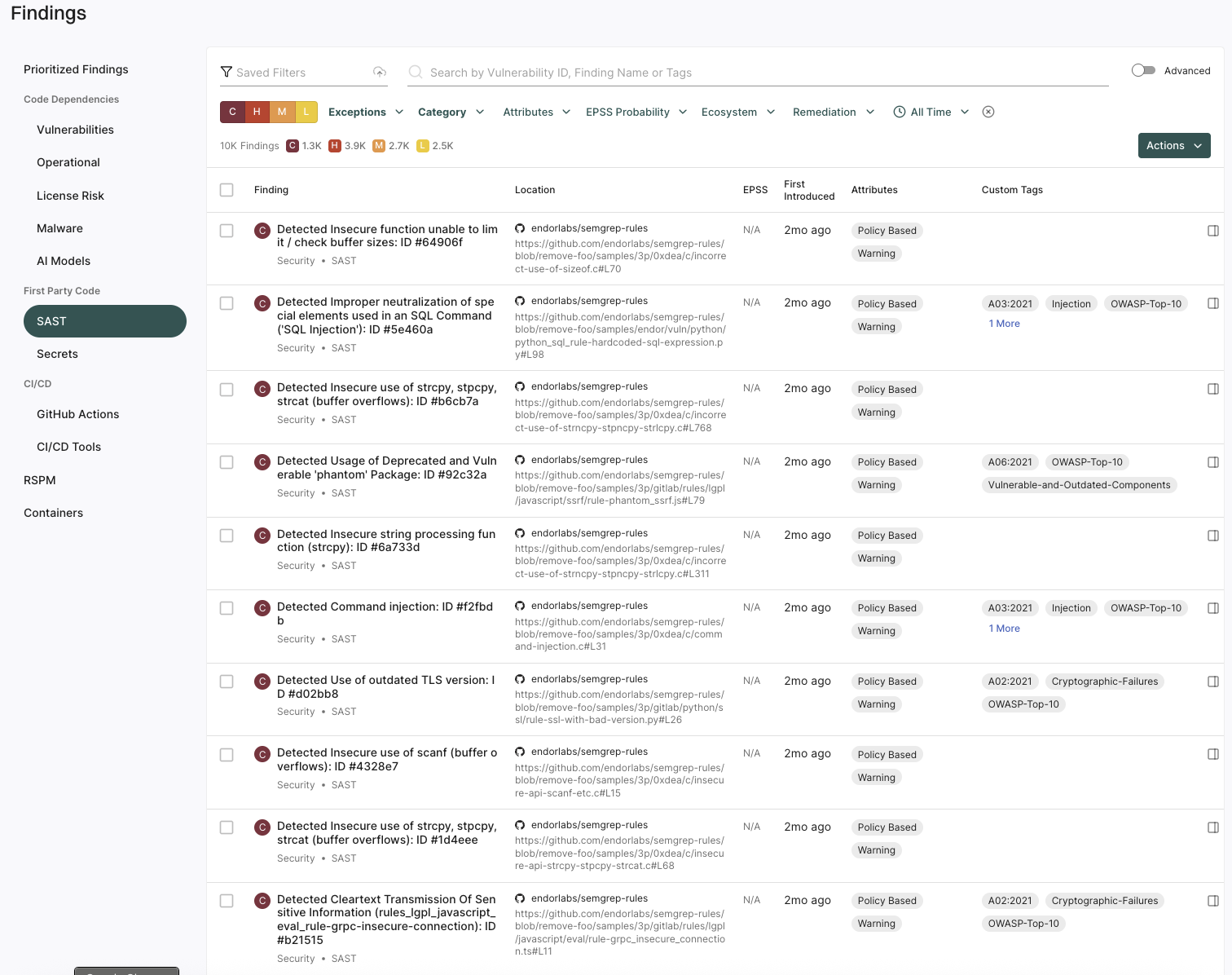
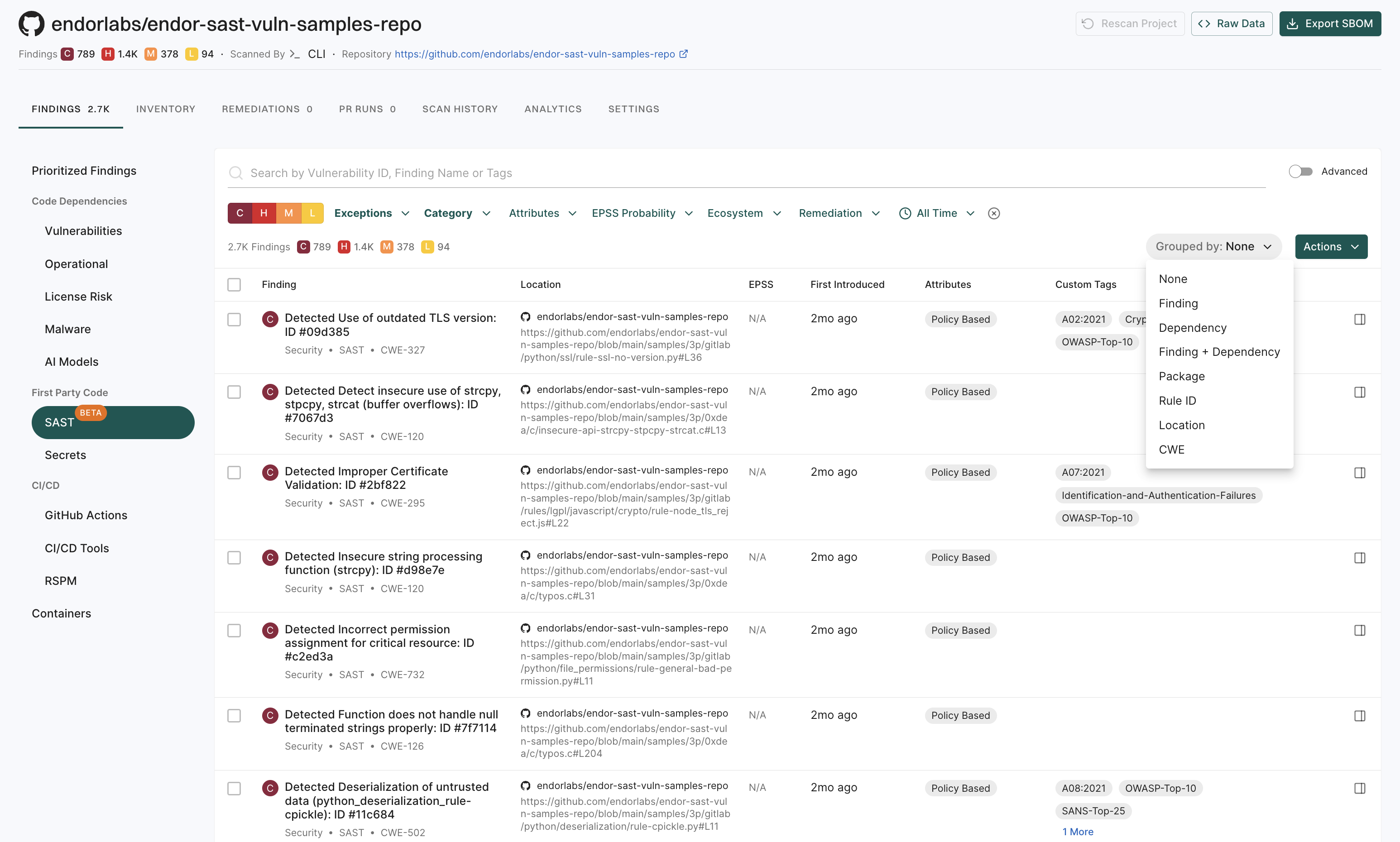
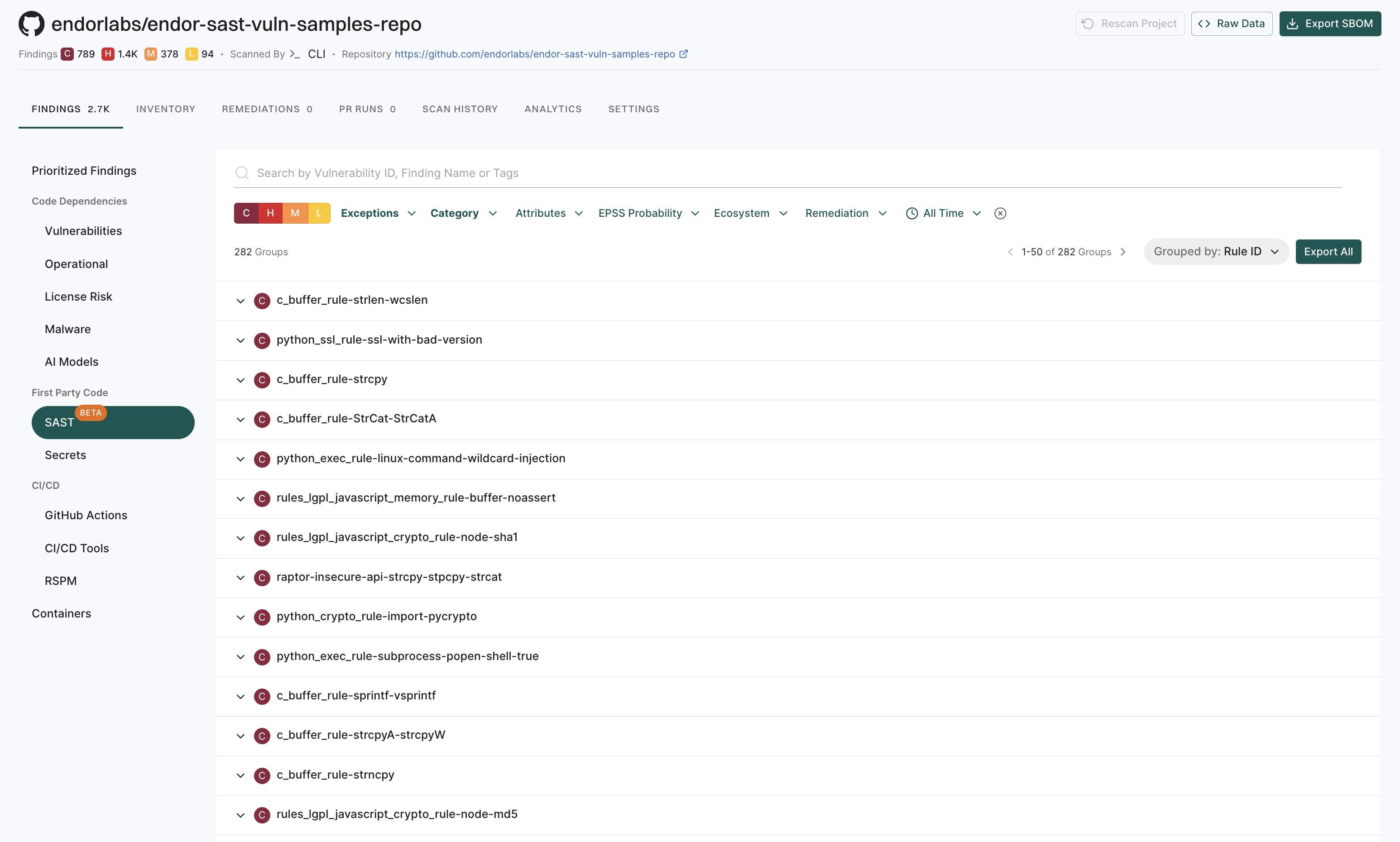
Login to Endor Labs to view the findings of a SAST scan. See SAST Findings for more information.
You can create exception policies to exclude results from the findings page. See create exception policy for more information.
You can create a finding policy using predefined templates to control which SAST results appear as findings. See SAST policies for more information.
SAST severity matrix
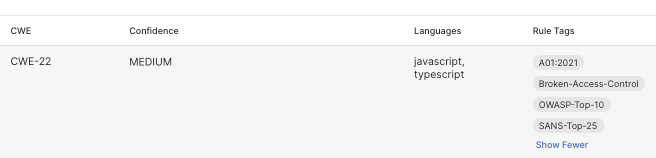
Endor Labs determines the severity of findings by combining two factors from the SAST rule: impact and confidence. Impact measures the potential consequences if a security issue were to be exploited. Confidence represents how certain the system is that a detected pattern indicates a genuine security issue rather than a false positive.
The following matrix shows how Endor Labs resolves severity by combining impact and confidence.
| Medium |
High |
Critical |
| Low |
Medium |
High |
| Low |
Low |
Medium |
|
Language support
Endor Labs supports single-function analysis for the following languages through curated rules and custom user rules:
Apex Bash C Cairo Circom Clojure C++ C# Dart Dockerfile Elixir Generic Go Hack HTML Java JavaScript JSON Jsonnet Julia Kotlin Lisp Lua Move OCaml PHP PromQL Protobuf Python QL R Regex Ruby Rust Scala Scheme Solidity Swift Terraform TypeScript XML YAML
SAST scan in Endor Labs
Endor Labs offers several ways to run SAST scans based on your project setup.
- AI-analyzed SAST scan with endorctl
- SAST scan in monitoring scans
- AI-analyzed SAST scan in monitoring scans
- SAST scan in Endor Labs GitHub Action
AI-analyzed SAST scan with endorctl
You can run AI-analyzed SAST scans using endorctl by adding the --ai-sast-analysis=agent-fallback flag to your scan command. The AI agent automatically classifies findings as true positives or false positives, reducing manual triage effort. See Run a SAST scan for more information.
SAST scan in monitoring scans
You can enable SAST scans when you configure monitoring or supervisory scans using the Endor Labs GitHub App, Azure DevOps App, Bitbucket App, and GitLab App. See Monitoring scans for more information. To disable the storage of code snippet in SAST scans for monitoring scans, you need to create a scan profile for your monitoring scan with disable code snippet storage as enabled. This setting applies to all scans that you use this scan profile, not just the monitoring scans.
AI-analyzed SAST scan in monitoring scans
Create or edit a scan profile, and select Enable the false positive reduction agent to enable AI SAST analysis for false positive reduction in monitoring scans. You need to associate this scan profile with your project. See Configure scan profile through Endor Labs user interface for more information.
SAST scan in Endor Labs GitHub Action
You can also enable SAST scan in the Endor Labs GitHub Action. Set the scanning parameter, scan_sast as true. To disable code snippet storage for SAST scans, set disable_code_snippet_storage as true. See Scan with GitHub Actions for more information.
SAST incremental scans
You can use the --pr-incremental flag to perform an incremental scan on your pull requests or merge requests for SAST. In monitoring scans, incremental scans are done by default for PR scans. Endor Labs only scans the files that have changed since the last scan on the baseline branch. Endor Labs computes a diff between the target branch and the baseline branch to identify the changed files. Any modified file is sent through Opengrep to fully scan for SAST issues, and unchanged files are skipped. Endor Labs does not perform chunk-level or line-level code diff analysis for SAST. If there are more than 1000 modified files, Endor Labs performs a complete scan.