Azure Pipelines is a continuous integration and continuous delivery (CI/CD) service available in Azure DevOps ecosystem. It facilitates continuous integration, continuous testing, and continuous deployment for seamless building, testing, and delivery of software.
You can use Azure extension from Endor Labs to include Endor Labs within your Azure pipelines or add steps in your pipeline to manually download and use Endor Labs in your runner.
Complete the prerequisites
Ensure that you complete the following prerequisites before you proceed.
Set up an Endor Labs tenant
You must have an Endor Labs tenant set up for your organization. You can also set up namespaces according to your requirements. See Set up namespaces
Configure Endor Labs authentication
Configure an API key and secret for authentication. See managing API keys for more information on generating an API key for Endor Labs. Store API key and secret as environment variables, ENDOR_API_CREDENTIALS_KEY and ENDOR_API_CREDENTIALS_SECRET.
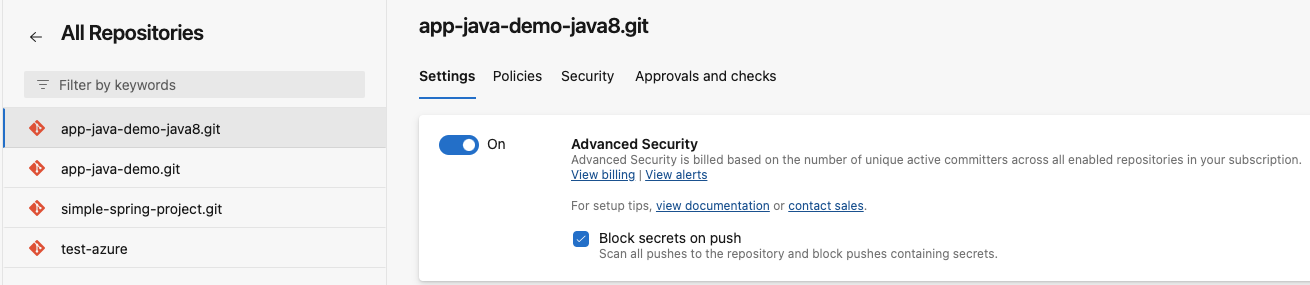
Enable Advanced Security in Azure
You need to enable Advanced Security in your Azure repository to view results in Azure.
- Log in to Azure and open Project Settings.
- Navigate to Repos > Repositories in the left navigation panel.
- Select your repository.
- Enable Advanced Security.
Integrate Endor Labs with Azure pipelines with the Azure extension
To integrate Endor Labs with Azure pipelines, you need to set up the Azure extension. After you set up the extension, you can configure your pipline to use Endor Labs.
Note
The Endor Labs Azure extension requirescode read, build read, and execute permissions.
Set up the Azure extension
- Install the Endor Labs extension from the Visual Studio Marketplace.
- Log in Azure DevOps and select your project.
- Select Project Settings from the left sidebar.
- Select Service Connections under Pipelines.
- Click Create service connection.
- Select Endor Labs and click Next.
- Enter
https://api.endorlabs.comas the Server URL. - Enter the API Key and API Secret that you created.
- Enter the service connection name. The name you enter here is to be used inside the Azure pipeline.
- Optionally, you can enter service management reference and description.
- Select Grant access permission to all pipelines to provide access to Endor Lab’s service connection to your pipelines.
Warning
Ensure that you select this option if you want to use Endor Labs with your pipelines. Unless you enable the service connection, Endor Labs will not be available to your pipelines. - Click Save.
Configure Azure pipeline to use Endor Labs
-
Create
azure-pipelines.ymlfile in your project, if it doesn’t exist and enter values according to your requirement. -
In the
azure-pipelines.ymlfile, enter the task,EndorLabsScan@0, with the service connection name, Endor Labs namespace, and the SARIF file name.For example:
steps: - task: EndorLabsScan@0 inputs: serviceConnectionEndpoint: 'Endor' namespace: 'demo' sarifFile: 'scanresults.sarif' -
Enter the task,
AdvancedSecurity-Publish@1, if you wish to publish the scan results, which you can view under the Advanced Security tab in Azure DevOps.steps: - task: AdvancedSecurity-Dependency-Scanning@1 displayName: Publish scan dependencies to Advanced Security inputs: SarifsInputDirectory: $(Build.SourcesDirectory)\
After a successful run of the pipeline, you can view the results in Azure.
Endor Labs scan parameters
You can use the following input parameters in the EndorLabsScan@0 task.
| Parameter | Description |
|---|---|
additionalArgs |
Add custom arguments to the endorctl scan command. |
phantomDependencies |
Set to true to enable phantom dependency analysis. (Default: false) |
sarifFile |
Set to a location on your hosted agent to output the findings in SARIF format. |
scanDependencies |
Scan Git commits and generate findings for all dependencies. (Default: true) |
scanPath |
Set the path to the directory to scan. (Default: .) |
scanSast |
Set to true to enable SAST scan. (Default: false) |
scanSecrets |
Scan source code repository and generate findings for secrets. See also scanGitLogs. (Default: false) |
scanGitLogs |
Perform a more complete and detailed scan of secrets in the repository history. Requires scanSecrets to be set as true. (Default: false) |
scanTools |
Scan source code repository for CI/CD tools. (Default: false) |
tags |
Specify a list of user-defined tags to add to this scan. Tags help you search and filter scans. |
scanPackage |
Scan a specified artifact or a package. The path to an artifact must be set with scanPath. (Default: false) |
scanContainer |
Scan a specified container image. Set the image with image and a project with projectName. (Default: false) |
projectName |
Specify a project name for a container image scan or for a package scan. |
image |
Specify a container image to scan. |
Example Workflow
The following example workflow initiates a scan where all dependencies are scanned along with secrets. The findings are tagged with Azure. The scan generates a SARIF file and uploads to GitHub Advanced Security.
trigger:
- none
pool:
name: Azure Pipelines
vmImage: "windows-latest"
steps:
- task: EndorLabsScan@0
inputs:
serviceConnectionEndpoint: 'endorlabs-service-connection'
namespace: 'endor'
sarifFile: 'scanresults.sarif'
scanSecrets: 'true'
tags: `Azure`
- task: AdvancedSecurity-Publish@1
displayName: Publish 'scanresults.sarif' to Advanced Security
inputs:
SarifsInputDirectory: $(Build.SourcesDirectory)\
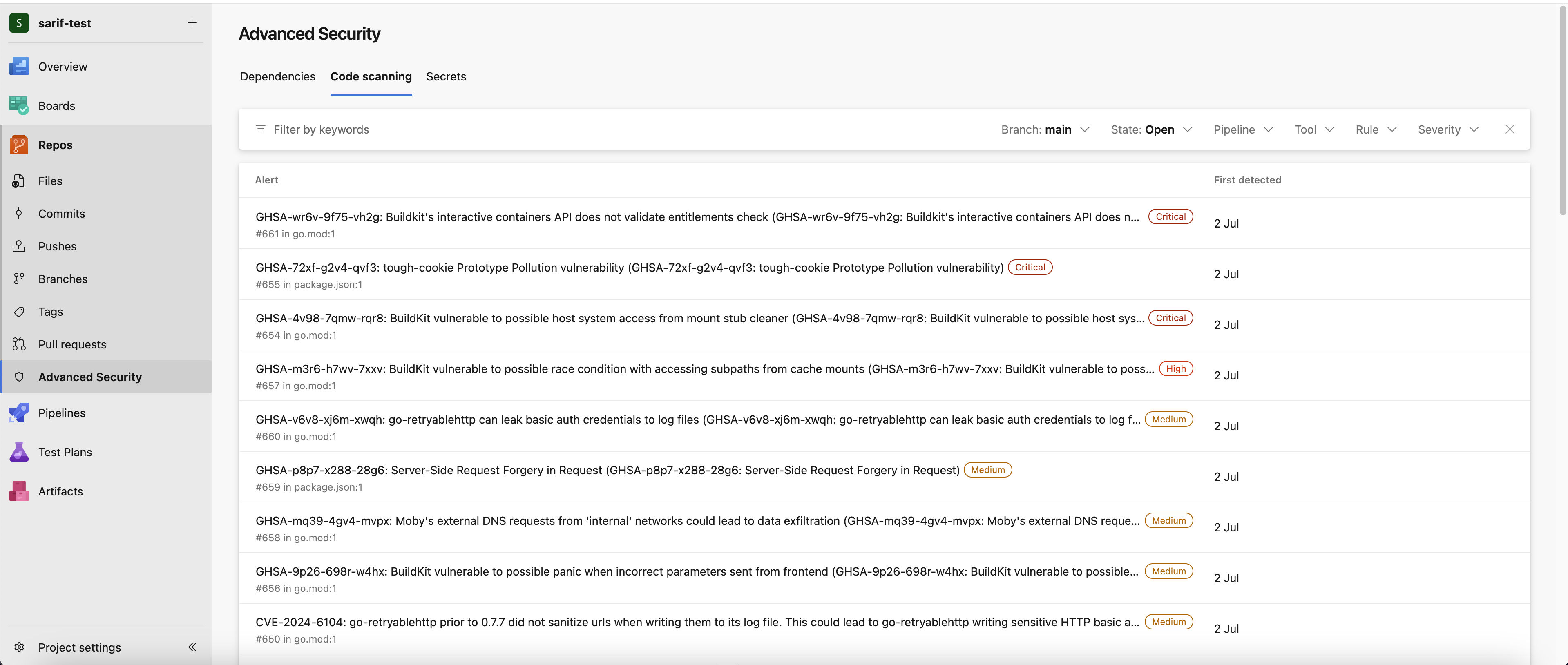
View scan results in Azure
After the pipeline runs, you can view the scan results in Azure.
-
Log in to Azure and navigate to your projects.
-
Select Repos > Advanced Security to view the scan results.
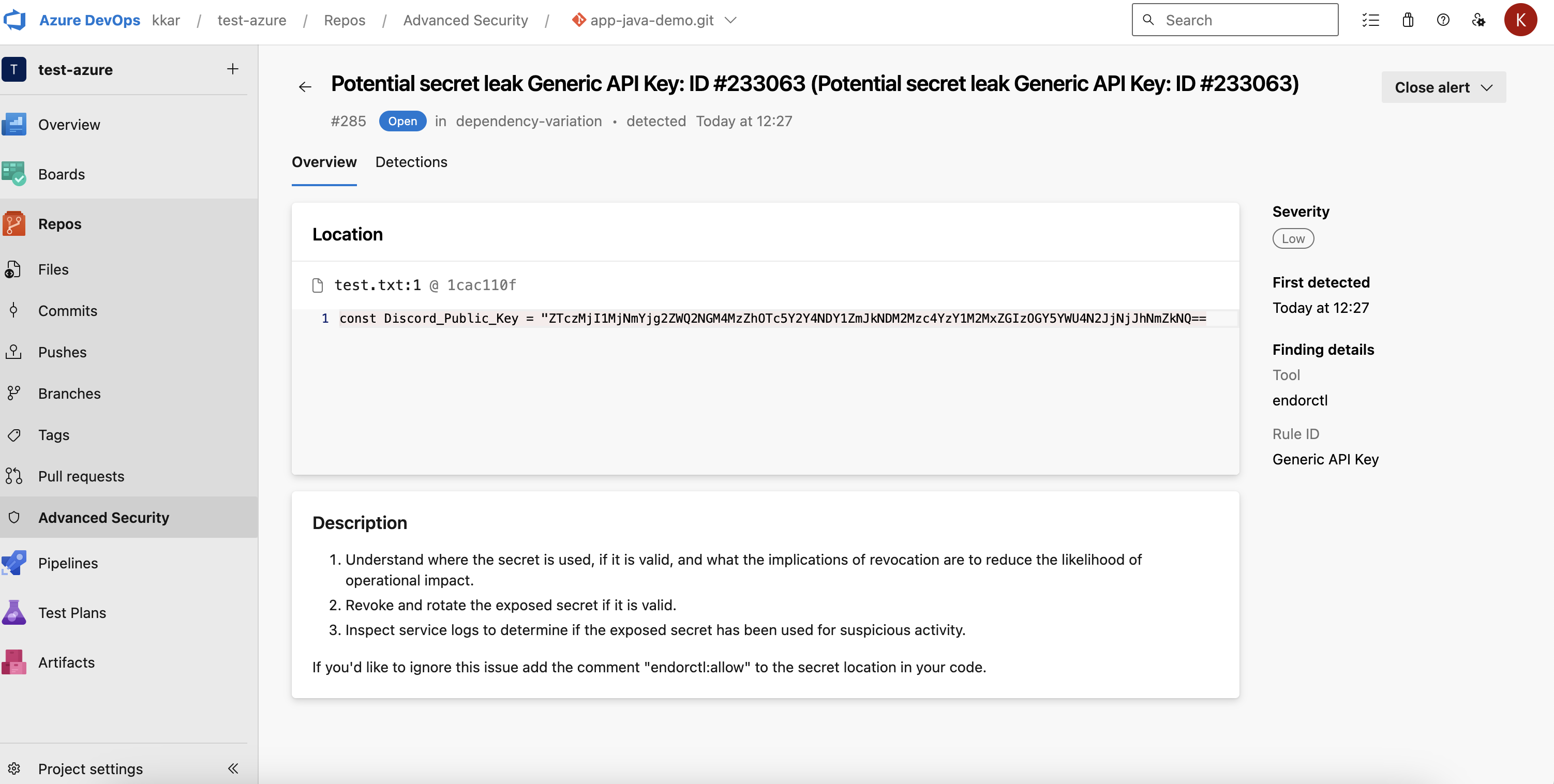
-
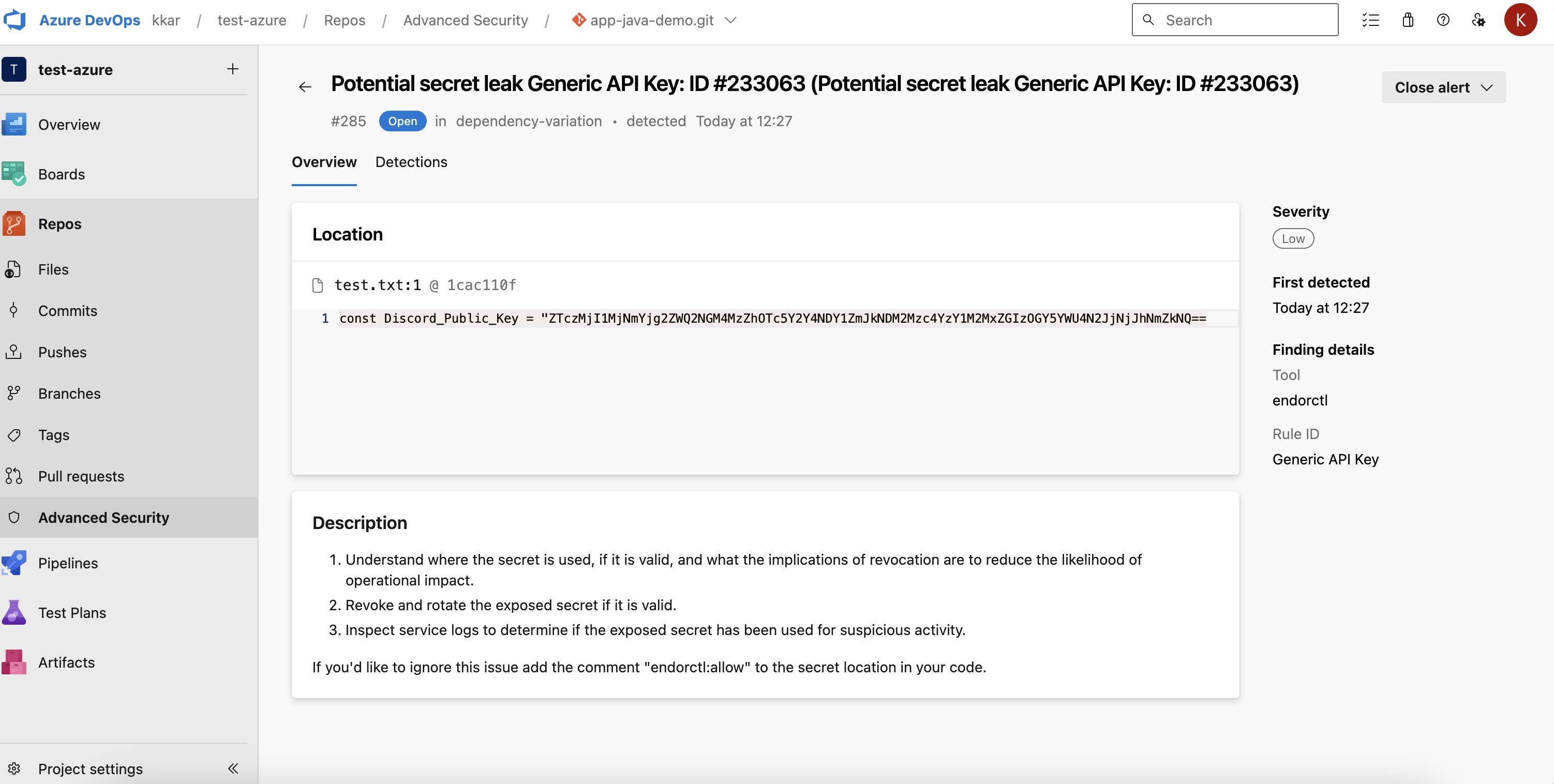
Click an alert to view more details.
-
If you ran endorctl with
--secretsflag, you can view if there are any secret leaks.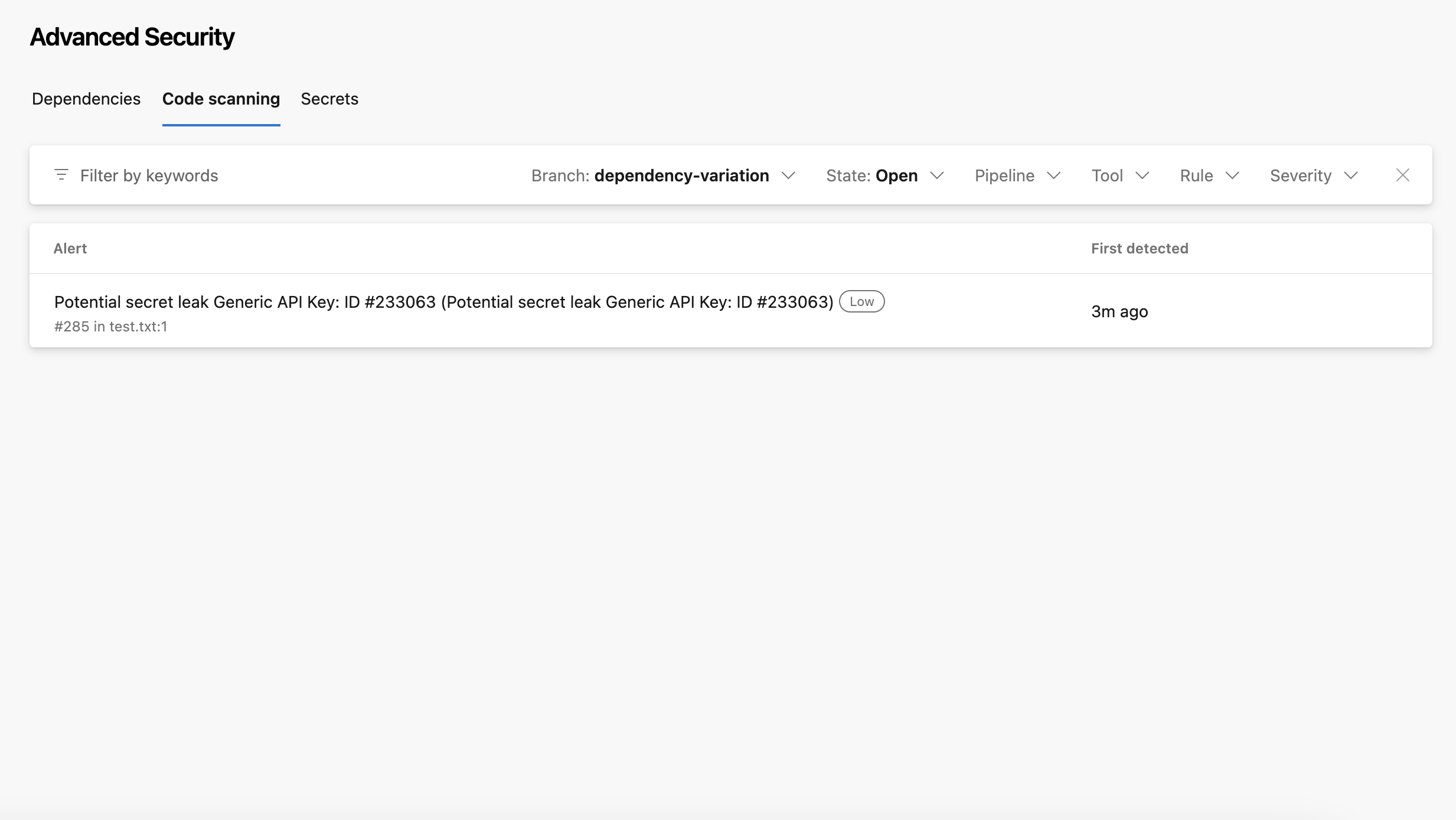
Click the entry to view more details.
Download and use endorctl in Azure pipeline
You can also choose to set up your pipeline to download endorctl and scan using Endor Labs without using the Azure extension.
Configure Endor Labs variables in the pipeline
You can manage Endor Labs variables centrally by configuring them within your Azure project. You can assign these variables to various pipelines.
- Log in to Azure and select Pipelines > Library.
- Click +Variable Group to add a new variable group for Endor Labs.
- Enter a name for the variable group, for example,
tenant-variables, and click Add under Variables. - Add the following variables.
ENDOR_API_CREDENTIALS_KEYENDOR_API_CREDENTIALS_SECRETNAMESPACE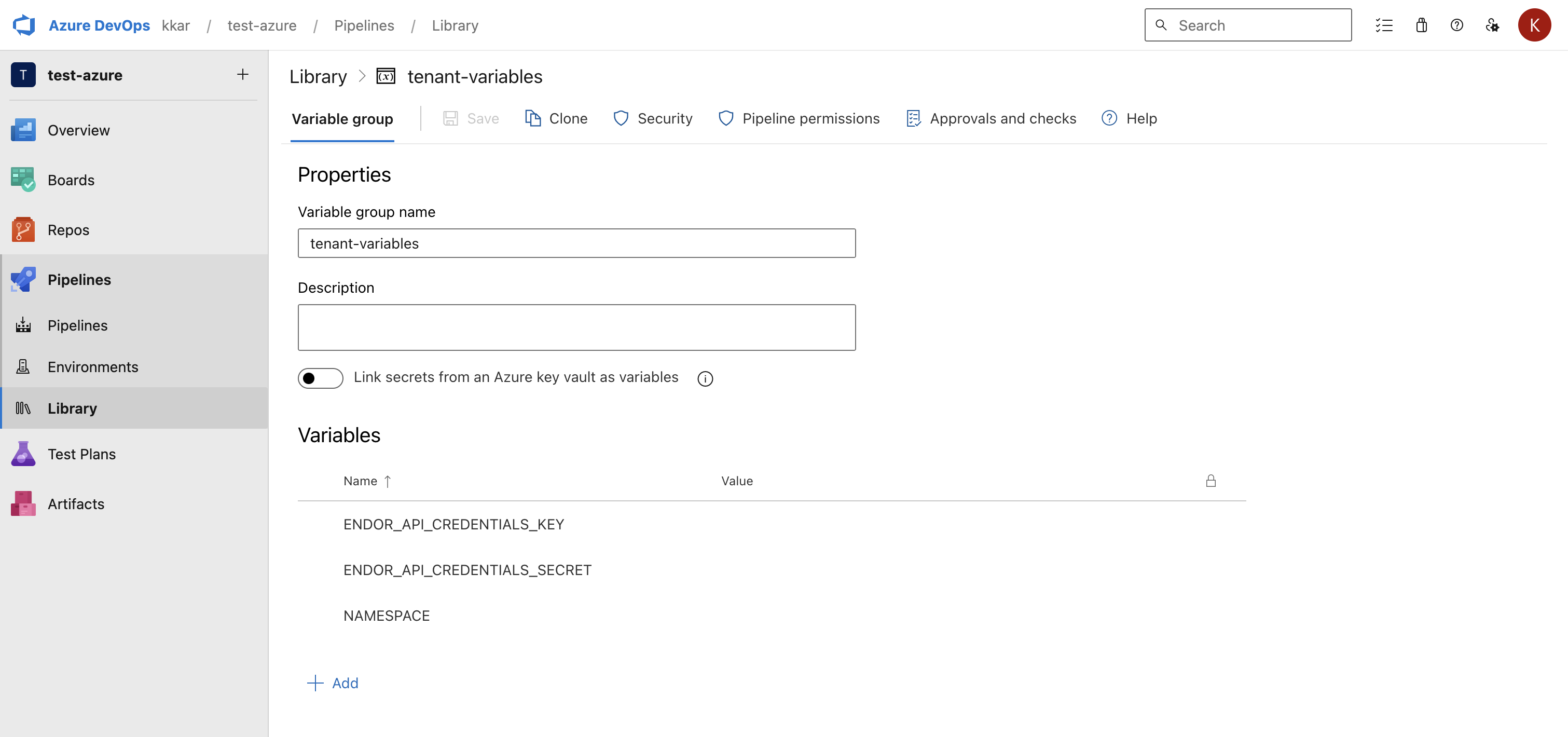
- Select the variable group that you created.
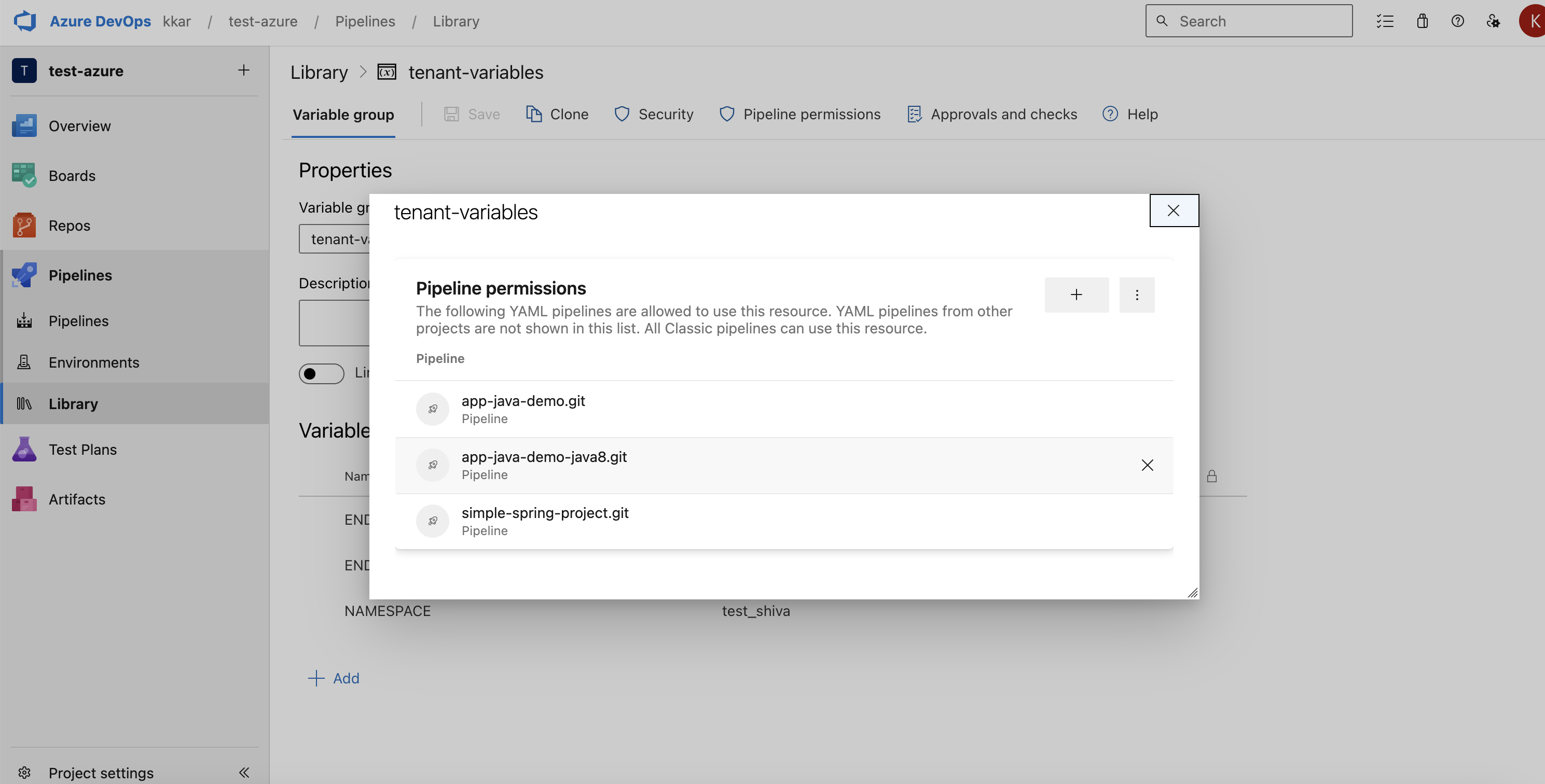
- Click Pipeline Permissions.
- Click + to add the pipelines in which you want to use the variable group.
Configure your Azure pipeline
- Create
azure-pipelines.ymlfile in your project, if it doesn’t exist. - In the
azure-pipelines.ymlfile, customize the job configuration based on your project’s requirements. - Adjust the image field to use the necessary build tools for constructing your software packages, and align your build steps with those of your project. For example, update the node pool settings based on your operating system.
pool:
name: Default
vmImage: "windows-latest"
pool:
name: Default
vmImage: "ubuntu-latest"
pool:
name: Default
vmImage: "macOS-latest"
-
Update your default branch from main if you do not use main as the default branch name.
-
Modify any dependency or artifact caches to align with the languages and caches used by your project.
-
Enter the following steps in the
azure-pipelines.ymlfile to download endorctl.
- bash: |
echo "Downloading latest version of endorctl"
VERSION=$(curl https://api.endorlabs.com/meta/version | grep -o '"Version":"[^"]*"' | sed 's/.*"Version":"\([^"]*\)".*/\1/')
curl https://api.endorlabs.com/download/endorlabs/"$VERSION"/binaries/endorctl_"$VERSION"_windows_amd64.exe -o endorctl.exe
echo "$(curl -s https://api.endorlabs.com/sha/latest/endorctl_windows_amd64.exe) endorctl" | sha256sum -c
if [ $? -ne 0 ]; then
echo "Integrity check failed"
exit 1
fi
- bash: |
echo "Downloading latest version of endorctl"
VERSION=$(curl https://api.endorlabs.com/meta/version | grep -o '"Version":"[^"]*"' | sed 's/.*"Version":"\([^"]*\)".*/\1/')
curl https://api.endorlabs.com/download/endorlabs/"$VERSION"/binaries/endorctl_"$VERSION"_linux_amd64 -o endorctl
echo "$(curl -s https://api.endorlabs.com/sha/latest/endorctl_linux_amd64) endorctl" | sha256sum -c
if [ $? -ne 0 ]; then
echo "Integrity check failed"
exit 1
fi
- bash: |
echo "Downloading latest version of endorctl"
VERSION=$(curl https://api.endorlabs.com/meta/version | grep -o '"Version":"[^"]*"' | sed 's/.*"Version":"\([^"]*\)".*/\1/')
curl https://api.endorlabs.com/download/endorlabs/"$VERSION"/binaries/endorctl_"$VERSION"_macos_arm64 -o endorctl
echo "$(curl -s https://api.endorlabs.com/sha/latest/endorctl_macos_arm64) endorctl" | shasum -a 256 --check
if [ $? -ne 0 ]; then
echo "Integrity check failed"
exit 1
fi
-
Enter the steps to build your project if your project needs building and setup steps.
-
Enter the following step in the
azure-pipelines.ymlfile to run endorctl scan to generate the SARIF file.You can run endorctl scan with options according to your requirement, but you must include the
-soption to generate the SARIF file.For example, use the
--secretsflag to scan for secrets.
- script: |
.\endorctl.exe scan -n $(NAMESPACE) -s scanresults.sarif
env:
ENDOR_API_CREDENTIALS_KEY: $(ENDOR_API_CREDENTIALS_KEY)
ENDOR_API_CREDENTIALS_SECRET: $(ENDOR_API_CREDENTIALS_SECRET)
- script: |
.\endorctl scan -n $(NAMESPACE) -s scanresults.sarif
env:
ENDOR_API_CREDENTIALS_KEY: $(ENDOR_API_CREDENTIALS_KEY)
ENDOR_API_CREDENTIALS_SECRET: $(ENDOR_API_CREDENTIALS_SECRET)
- script: |
.\endorctl scan -n $(NAMESPACE) -s scanresults.sarif
env:
ENDOR_API_CREDENTIALS_KEY: $(ENDOR_API_CREDENTIALS_KEY)
ENDOR_API_CREDENTIALS_SECRET: $(ENDOR_API_CREDENTIALS_SECRET)
- Enter the following task in the
azure-pipelines.ymlto publish the scan results.
- task: AdvancedSecurity-Publish@1
displayName: Publish '.\sarif\scanresults.sarif' to Advanced Security
inputs:
SarifsInputDirectory: $(Build.SourcesDirectory)\
After a successful run of the pipeline, you can view the results in Azure.
Azure Pipeline Examples
trigger:
- none
pool:
name: Azure Pipelines
vmImage: "windows-latest"
variables:
- group: tenant-variables
steps:
# All steps related to building of the project should be before this step.
# Implement and scan with Endor Labs after your build is complete.
- bash: |
- bash: |
echo "Downloading latest version of endorctl"
VERSION=$(curl https://api.endorlabs.com/meta/version | grep -o '"Version":"[^"]*"' | sed 's/.*"Version":"\([^"]*\)".*/\1/')
curl https://api.endorlabs.com/download/endorlabs/"$VERSION"/binaries/endorctl_"$VERSION"_windows_amd64.exe -o endorctl.exe
echo "$(curl -s https://api.endorlabs.com/sha/latest/endorctl_windows_amd64.exe) endorctl" | sha256sum -c
if [ $? -ne 0 ]; then
echo "Integrity check failed"
exit 1
fi
displayName: 'Downloading latest version of endorctl'
continueOnError: false
- script: |
.\endorctl.exe scan -n $(NAMESPACE) -s scanresults.sarif
displayName: 'Run a scan against the repository using your API key & secret pair'
env:
ENDOR_API_CREDENTIALS_KEY: $(ENDOR_API_CREDENTIALS_KEY)
ENDOR_API_CREDENTIALS_SECRET: $(ENDOR_API_CREDENTIALS_SECRET)
- task: AdvancedSecurity-Publish@1
displayName: Publish '.\sarif\scanresults.sarif' to Advanced Security
inputs:
SarifsInputDirectory: $(Build.SourcesDirectory)\
trigger:
- none
pool:
name: Azure Pipelines
vmImage: "ubuntu-latest"
variables:
- group: tenant-variables
steps:
# All steps related to building of the project should be before this step.
# Implement and scan with Endor Labs after your build is complete.
- bash: |
- bash: |
echo "Downloading latest version of endorctl"
VERSION=$(curl https://api.endorlabs.com/meta/version | grep -o '"Version":"[^"]*"' | sed 's/.*"Version":"\([^"]*\)".*/\1/')
curl https://api.endorlabs.com/download/endorlabs/"$VERSION"/binaries/endorctl_"$VERSION"_linux_amd64 -o endorctl
echo "$(curl -s https://api.endorlabs.com/sha/latest/endorctl_linux_amd64) endorctl" | sha256sum -c
if [ $? -ne 0 ]; then
echo "Integrity check failed"
exit 1
fi
## Modify the permissions of the binary to ensure it is executable
chmod +x ./endorctl
## Create an alias of the endorctl binary to ensure it is available in other directories
alias endorctl="$PWD/endorctl"
displayName: 'Downloading latest version of endorctl'
continueOnError: false
- script: |
./endorctl scan -n $(NAMESPACE) -s scanresults.sarif
displayName: 'Run a scan against the repository using your API key & secret pair'
env:
ENDOR_API_CREDENTIALS_KEY: $(ENDOR_API_CREDENTIALS_KEY)
ENDOR_API_CREDENTIALS_SECRET: $(ENDOR_API_CREDENTIALS_SECRET)
- task: AdvancedSecurity-Publish@1
displayName: Publish '.\sarif\scanresults.sarif' to Advanced Security
inputs:
SarifsInputDirectory: $(Build.SourcesDirectory)/
trigger:
- none
pool:
name: Azure Pipelines
vmImage: "macos-latest"
variables:
- group: tenant-variables
steps:
# All steps related to building of the project should be before this step.
# Implement and scan with Endor Labs after your build is complete.
- bash: |
echo "Downloading latest version of endorctl"
VERSION=$(curl https://api.endorlabs.com/meta/version | grep -o '"Version":"[^"]*"' | sed 's/.*"Version":"\([^"]*\)".*/\1/')
curl https://api.endorlabs.com/download/endorlabs/"$VERSION"/binaries/endorctl_"$VERSION"_macos_arm64 -o endorctl
echo "$(curl -s https://api.endorlabs.com/sha/latest/endorctl_macos_arm64) endorctl" | shasum -a 256 --check
if [ $? -ne 0 ]; then
echo "Integrity check failed"
exit 1
fi
## Modify the permissions of the binary to ensure it is executable
chmod +x ./endorctl
## Create an alias of the endorctl binary to ensure it is available in other directories
alias endorctl="$PWD/endorctl"
displayName: 'Downloading latest version of endorctl'
continueOnError: false
- script: |
./endorctl scan -n $(NAMESPACE) -s scanresults.sarif
displayName: 'Run a scan against the repository using your API key & secret pair'
env:
ENDOR_API_CREDENTIALS_KEY: $(ENDOR_API_CREDENTIALS_KEY)
ENDOR_API_CREDENTIALS_SECRET: $(ENDOR_API_CREDENTIALS_SECRET)
- task: AdvancedSecurity-Publish@1
displayName: Publish '.\sarif\scanresults.sarif' to Advanced Security
inputs:
SarifsInputDirectory: $(Build.SourcesDirectory)/